
ZeroLogon Exploit: Threat to Active Directory and Domain Controllers
The ZeroLogon exploit is currently one of the most dangerous cyber threats used by malicious actors to attack Microsoft Active Directory environments. This exploit is registered under the identifier CVE-2020-1472 and poses a serious risk to Microsoft domain controllers.
The key feature of ZeroLogon is that attackers can gain full access to a domain controller without any authentication. This allows them to manage all user accounts within the network, create new ones, modify existing ones, and distribute malware.
ZeroLogon exploits a vulnerability in the Netlogon Remote Protocol (MS-NRPC), which is designed to manage authentication and authorization processes within Active Directory. A breach of this protocol makes the domain controller vulnerable.
According to cybersecurity researchers from Group-IB, attackers can exploit this vulnerability by sending specially crafted Netlogon requests, which allow them to change the domain controller’s password. This grants them administrative privileges.
In February 2024, following the shutdown of the ALPHV hacker group’s infrastructure, a new Ransomware-as-a-Service (RaaS) operation called RansomHub emerged. ALPHV’s closure occurred after a large-scale attack on the Change Healthcare system.
Amid increased law enforcement actions against major groups such as ALPHV and LockBit, RansomHub quickly expanded its operations and launched new partnership programs. This enabled cybercriminals to continue their activities.
Consequences of the ZeroLogon Exploit
The consequences of this attack can be extremely severe, as attackers gain the ability to:
- Seize network control – create new user accounts and modify existing ones.
- Spread malicious programs – upload ransomware and other malicious code into corporate networks.
- Encrypt data and extort ransom – attackers can encrypt critical business data and demand large sums for decryption.
How to Protect Against ZeroLogon?
To effectively defend against the ZeroLogon threat, organizations must take the following measures:
- Update domain controllers – install the latest security patches from Microsoft.
- Monitor Netlogon activity – track unknown or suspicious authentication attempts within the network.
- Implement Multi-Factor Authentication (MFA) – provide additional protection for administrator accounts.
- Segment the network – place critical servers in separate network segments to prevent malware spread.
- Use PowerShell scripts to monitor activity:
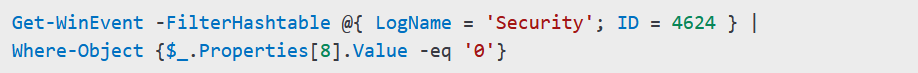
This script helps detect authentication attempts without credentials.
The ZeroLogon exploit is one of the most serious cyberattacks today. Organizations must strengthen their security measures to prevent potential attacks and protect their domain controllers. In the fight against new ransomware threats, it is crucial to remain vigilant and continuously monitor system security.



