
Vulnerability in WordPress plugin puts over 4 million websites at risk
A recently discovered critical security vulnerability in one of WordPress’s most popular plugins, Really Simple Security, has put more than 4 million websites at risk of potential hacking attacks. This major vulnerability has raised significant concerns among plugin users.
The vulnerability, identified as CVE-2024-10924, affects all plugin versions from 9.0.0 to 9.1.1.1, including the free, Pro, and multisite Pro versions. An error in the plugin’s two-factor authentication (2FA) feature allows attackers to bypass authentication and gain administrator-level access to the site, potentially leading to complete site compromise.
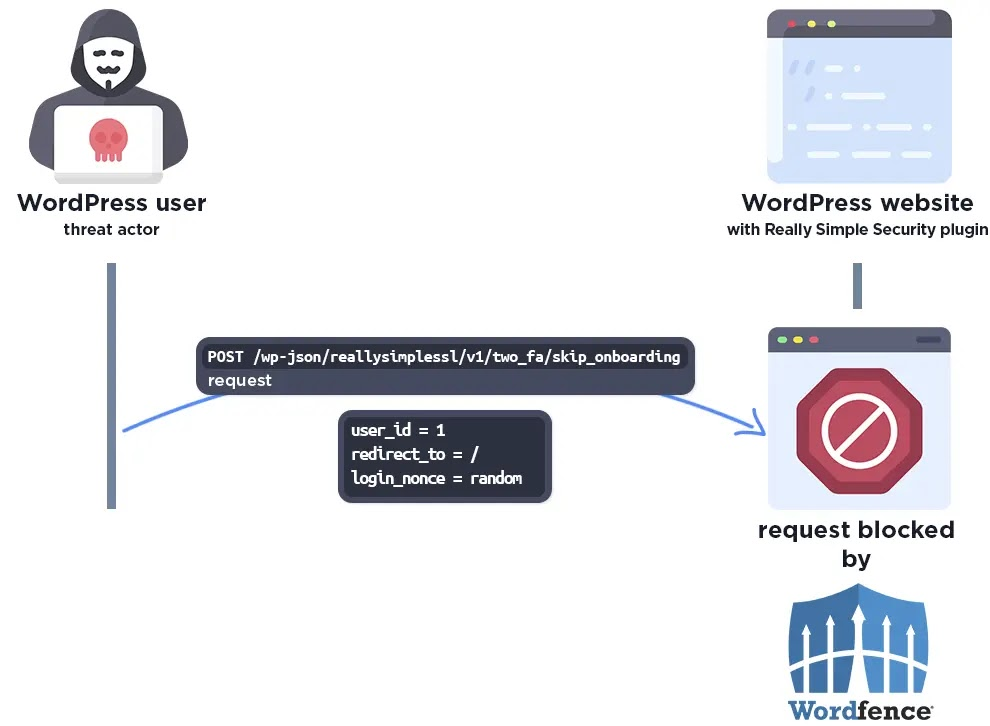
Really Simple Plugins was informed about the vulnerability on November 6 and promptly began working on a fix. Patches for the Pro versions were released on November 12, and for the free version on November 14. Considering the severity of the issue, the WordPress[.]org team implemented a forced update for all affected installations, upgrading them to version 9.1.2 or newer.
WordPress site administrators are strongly advised to update their plugins immediately, as automatic updates might not work for Pro users without a valid license. Security experts emphasize the importance of regularly updating plugins and staying informed about known vulnerabilities.
This incident serves as a stark reminder to WordPress users of the need for constant vigilance, timely updates, and robust security practices to safeguard websites against potential threats.



