Top 10 Dynamic Malware Analysis Tools for Identifying Modern Threats in 2025
Cybersecurity is one of the most pressing fields today. Modern malware is becoming increasingly sophisticated and can easily bypass traditional security mechanisms. To effectively combat such threats, dynamic analysis tools are used. These tools allow malware to be executed in a specially controlled environment, enabling real-time monitoring of its behavior.
Dynamic analysis is the process of running malware in a secure environment to observe its impact on a system. Unlike static analysis, which is limited to examining the software’s code, dynamic analysis allows for monitoring the program’s behavior during execution. This makes it an essential method for detecting complex or encrypted malware.
Dynamic analysis examines malware based on the following aspects:
- File system modifications: Creation of new files, modification, or deletion of existing files.
- Network activity: Identifying the servers the program connects to, whether it communicates with Command-and-Control (C2) servers, and if it transmits data.
- System impact: Changes to registry keys, processes, and services.
- API calls: The system calls the malware uses and their intended purpose.
- Evasion techniques: Mechanisms used by malware to bypass antivirus programs and analysis tools.
Modern malware is becoming more advanced. Therefore, effective countermeasures require dynamic analysis tools, which offer the following advantages:
- Detection of new threats: Uncovering encrypted or highly complex malware.
- Extraction of Indicators of Compromise (IoCs): Identifying malicious IP addresses, URLs, file hashes, and registry keys.
- Real-time data: Tracking how an attack unfolds and enabling rapid response.
- Comprehensive understanding of threats: Analyzing a program’s objectives and behavior.
- Threat intelligence: Profiling malware families and threat actor groups based on analysis results.
How is Dynamic Malware Analysis Performed?
- Preparing the environment: Setting up a virtual machine (VM) or a sandboxed environment.
- Executing the malware: Using tools such as ANY.RUN, Cuckoo Sandbox, or Joe Sandbox to monitor its activity.
- Observing behavior: Analyzing modifications to files, registry keys, processes, and network connections.
- Collecting IoCs: Extracting relevant information, such as IP addresses and other critical indicators.
- Generating a report: Evaluating the malware threat based on the collected data and implementing security measures.
Top 10 Dynamic Malware Analysis Tools (2025)
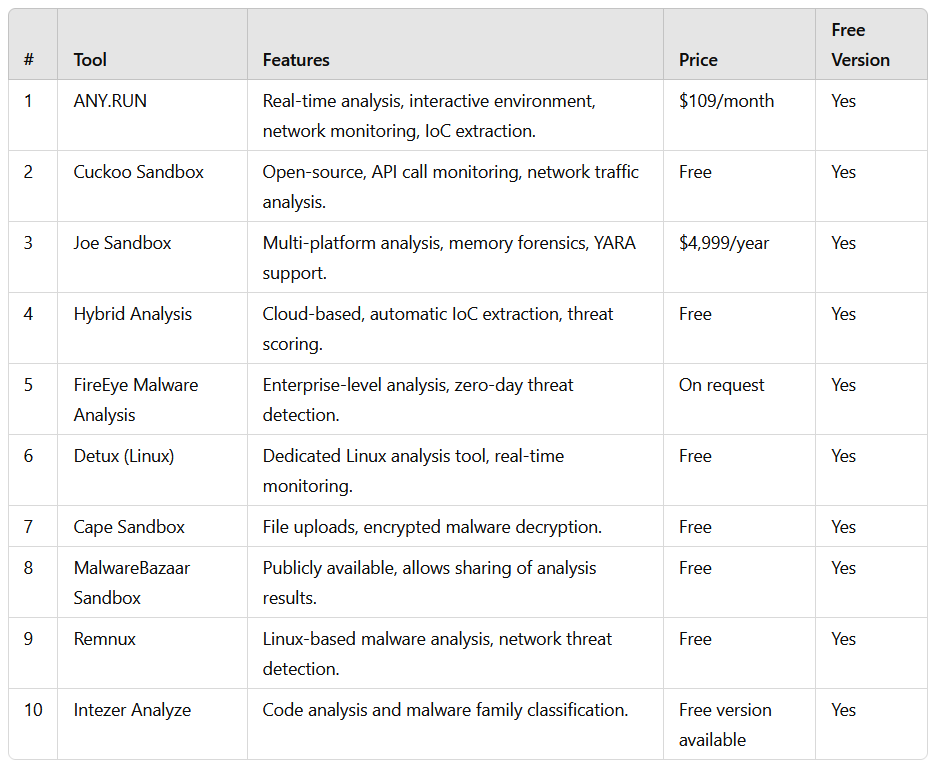
Dynamic malware analysis tools enable cybersecurity professionals to effectively detect modern threats. Each tool has its own unique advantages, and the choice of a suitable solution depends on the specific needs of a company.
If real-time interactive analysis is required, ANY.RUN is an excellent option. For those seeking a free and open-source solution, Cuckoo Sandbox is highly recommended.
For Linux-based systems, Detux or Remnux would be ideal, while Joe Sandbox or FireEye can be useful for advanced memory analysis. The key is to select the right tool for your requirements and ensure a high level of cybersecurity.