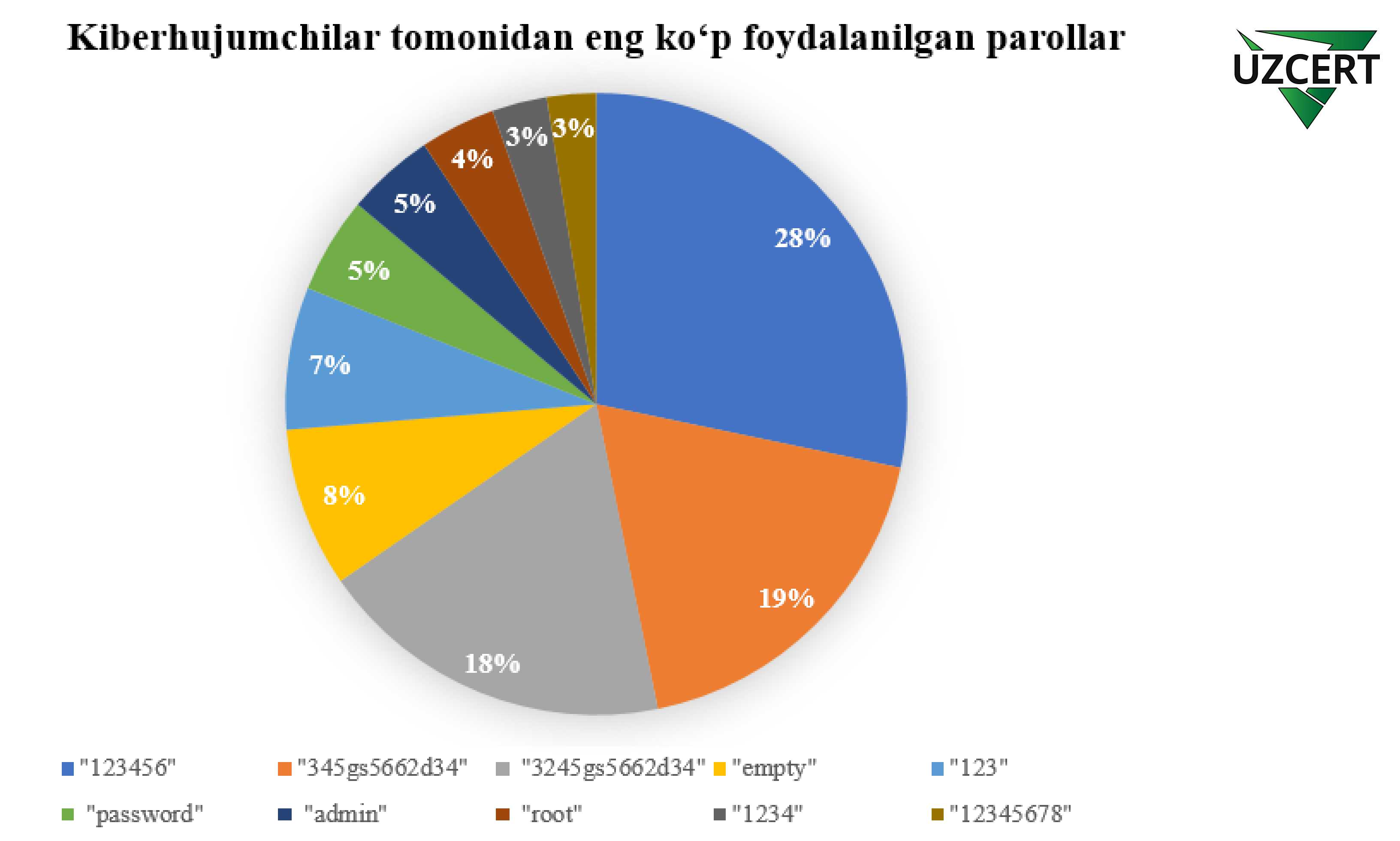
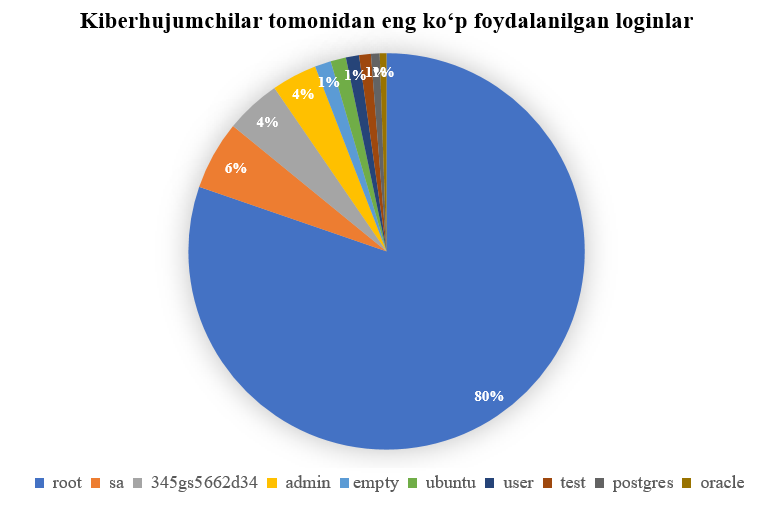
The most commonly used logins and passwords by cybercriminals in Uzbekistan in 2024
Today, the issue of cybersecurity has become one of the most relevant topics not only in the IT sector, but also in the daily life of every user. In particular, statistics revealed in Uzbekistan for 2024 showed that the list of logins and passwords most often used by cybercriminals revealed many security problems.
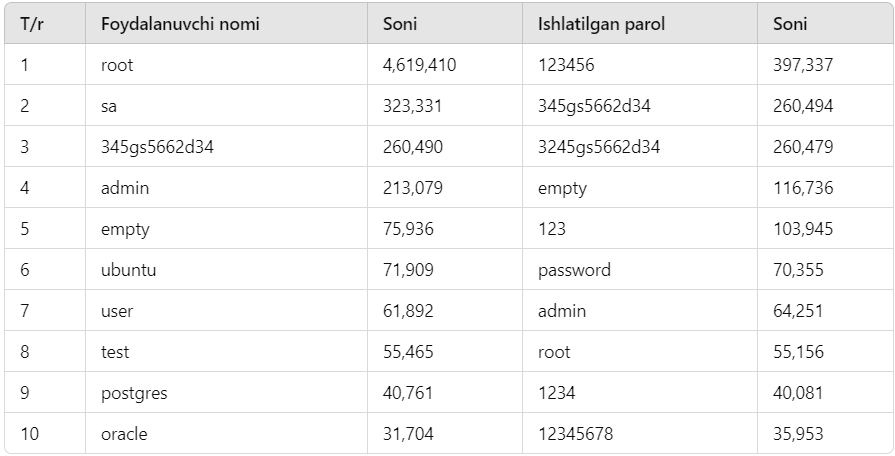
According to statistics, the use of very simple and easy-to-guess logins and passwords, due to the inattention of users, has created significant opportunities for cybercriminals. The figures below are a clear confirmation of this:
Among Usernames:
- The username “root” was used in login attempts 4,619,410 times.
- The username “sa” was used 323,331 times.
- Usernames like “admin” and “test” also remain popular among cybercriminals.
The Most Vulnerable Passwords:
- The password “123456” was used 397,337 times.
- The password “345gs5662d34” was used 260,494 times.
- Instances where the password was left “empty” (no password set) were observed 116,736 times.
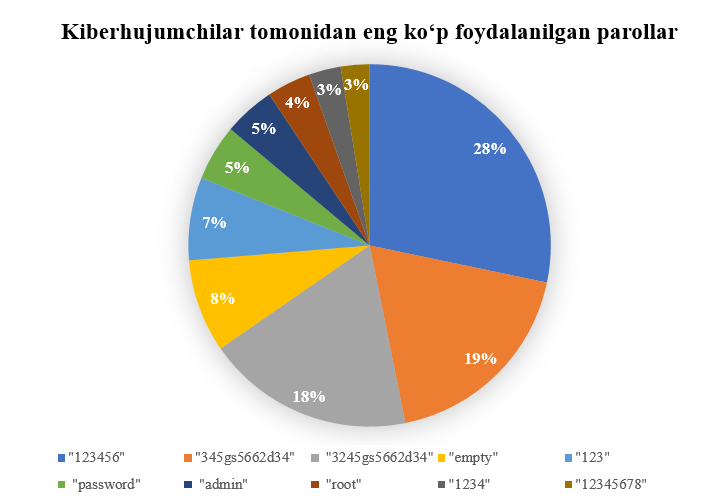
The most commonly used logins and passwords identified in Uzbekistan in 2024
The Danger of Weak Passwords
Using simple and easily guessable logins and passwords not only compromises your personal information but also puts your entire system at risk. Such vulnerabilities enable cybercriminals to gain unauthorized access to systems, steal data, or install malicious software.
For instance, the aforementioned “zero-click” attacks (attacks that do not require user interaction) are easily executed through systems with weak passwords.
Recommendations for Data Protection
To safeguard your personal and corporate data, it is recommended to follow these security measures:
- Use Strong Passwords. Avoid passwords that consist of simple words or sequential numbers. Instead, choose complex passwords that include uppercase and lowercase letters, numbers, and special characters.
- Use a Password Manager. If remembering passwords is difficult, use special applications to store them securely.
- Enable Two-Factor Authentication. This method requires additional verification when logging into the system.
- Regularly Update Your System. Updates are a vital part of cybersecurity as they address vulnerabilities.
- Set Up System Monitoring. Monitoring unusual activity in databases or networks can help prevent threats.
The analysis of the logins and passwords identified in 2024 shows that user negligence and failure to follow security practices have created numerous opportunities for cybercriminals to exploit.
A secure system is not just about technological tools but also the responsible behavior of users. Therefore, every user must take the protection of their data seriously.