
Serious vulnerability discovered in Kibana
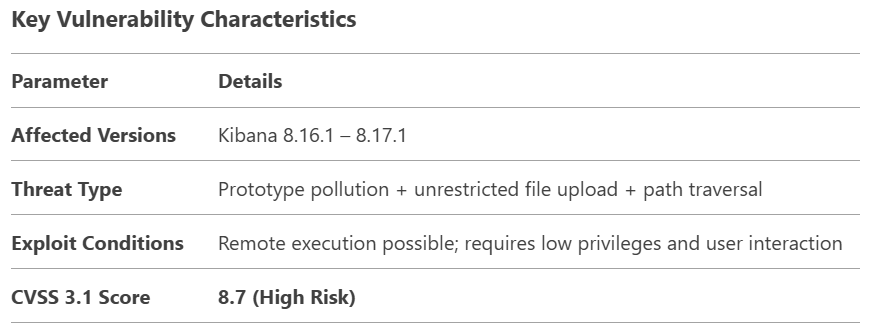
Elastic has issued an urgent security update for its Kibana data visualization platform, addressing a high-severity vulnerability that could allow attackers to execute arbitrary code. Tracked as CVE-2024-12556 with a CVSS score of 8.7 (High), this flaw affects Kibana versions 8.16.1 through 8.17.1
The security flaw stems from a prototype pollution vulnerability – a JavaScript/Node.js-specific weakness that enables attackers to manipulate object prototypes and alter application logic. When combined with unrestricted file uploads and path traversal techniques, malicious actors can:
- Upload files containing malicious payloads
- Write to unauthorized directories via path traversal
- Pollute object prototypes to modify server behavior
- Execute arbitrary code within Kibana’s environment
The vulnerability is remotely exploitable, requiring low privileges and some degree of user interaction for successful attacks.
Mitigation steps
✅ Immediately upgrade to Kibana 8.16.4 or 8.17.2 (or later).
✅ If immediate patching isn’t feasible, disable the Integration Assistant by adding this line to kibana.yml:

✅ Organizations running legacy versions (7.9.0 or older) should accelerate upgrade plans.
✅ Note: Kibana instances must be fully stopped before upgrading (rolling upgrades unsupported).
Security Recommendations
This incident highlights growing concerns about prototype pollution in JavaScript-based applications. Earlier this year, Elastic patched another critical prototype pollution flaw (CVE-2025-25015, CVSS 9.9). Best practices include:
- Prioritizing updates for data visualization platforms handling sensitive information
- Implementing strict access controls and user privilege management
- Monitoring for unusual activity in Kibana environments
⚠ Warning! While no active exploits have been detected, attackers may weaponize this vulnerability soon. Administrators should apply patches immediately!
🔒 Security is in your hands – update Kibana and safeguard your systems today!



