Newly Discovered PHP Vulnerability Threatens Windows Systems
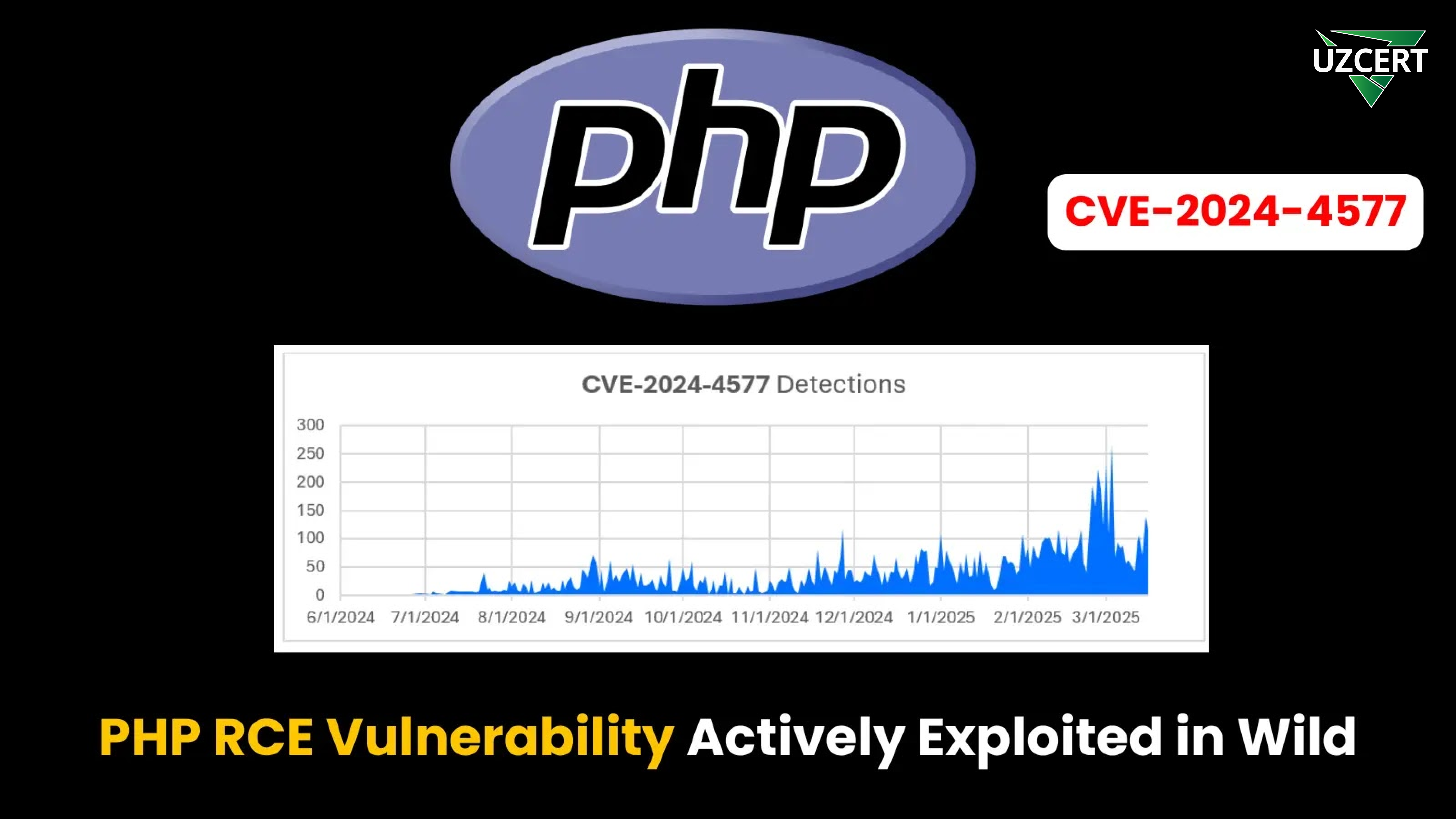
In the modern world of cybersecurity, any software vulnerability can pose a significant threat. The recently discovered CVE-2024-4577 vulnerability is a clear example of this. This flaw allows attackers to remotely execute malicious code through the PHP-CGI module on Windows systems. As a result, malicious software can be installed on servers, and their resources may be exploited for illegal purposes.
According to experts, this vulnerability is actively being used to deploy cryptocurrency miners and remote access tools (RATs). Therefore, all users are strongly advised to update their PHP versions as soon as possible and implement security measures.
The CVE-2024-4577 vulnerability affects PHP versions running in CGI mode on Windows systems. The issue arises when using certain character encodings because Windows’ “Best-Fit” mechanism replaces unrecognized characters with visually similar ones. As a result, the PHP-CGI module may misinterpret commands, allowing attackers to execute arbitrary code.
According to Bitdefender, the highest number of attacks exploiting this vulnerability have been observed in the following countries:
- Taiwan – 54.65%
- Hong Kong – 27.06%
- Brazil – 16.39%
- Japan – 1.57%
- India – 0.33%
These attacks are particularly widespread in regions where multi-byte character encodings are commonly used. However, experts warn that systems worldwide remain at risk.
Analysis shows that 15% of the attacks exploiting this vulnerability were initial test attempts, where attackers executed simple commands like “whoami” to verify the system’s susceptibility.
Another 15% of attacks focused on gathering system information, using built-in Windows commands to analyze the server’s internal structure.
The most dangerous attacks involved deploying cryptocurrency miners, accounting for 5% of the total attacks. In these cases, hackers installed XMRig to secretly use server resources for cryptocurrency mining. Additionally, remote access tools like Quasar RAT were installed, giving attackers full control over the compromised systems.
Cybersecurity researchers have also observed competition among attackers. Some cybercriminals not only exploited the vulnerability but also took measures to prevent rival hackers from accessing the same system. For example, some attackers modified firewall settings to block connections from specific IP addresses.
PHP developers have released updates that address this vulnerability:
- PHP 8.3.8
- PHP 8.2.20
- PHP 8.1.29
Therefore, it is crucial to update PHP immediately. If your server is still running PHP 8.0, PHP 7, or earlier versions, it is strongly recommended to upgrade to a supported version.
In addition to updating PHP, the following security measures should be implemented:
- Modify the PHP execution architecture:
- Switch from CGI mode to more secure alternatives like Mod-PHP, FastCGI, or PHP-FPM.
- Restrict access to administrative tools:
- Ensure that commands such as PowerShell can only be executed by authorized users.
- Implement continuous system monitoring:
- Use cybersecurity monitoring tools to detect suspicious activities at an early stage.
- Review firewall settings:
- Check if attackers have made unauthorized changes to security configurations.
- Create regular backups:
- Maintaining frequent backups will help restore the system in case of an attack.
The CVE-2024-4577 vulnerability poses a serious risk to Windows servers running PHP. Attackers are actively exploiting this flaw to deploy cryptocurrency miners, remote access tools, and gain full control over systems.
PHP developers have already released patches, and users are strongly advised to apply updates immediately. Additionally, ongoing monitoring, security enforcement, and migration from outdated PHP versions are essential.
If your Windows server runs PHP, following the above recommendations will help you protect your system from potential threats.



