
macOS Vulnerability: System Passwords at Risk!
Cybersecurity experts have recently discovered a critical vulnerability in the macOS operating system. This flaw could lead to the exposure of system passwords and confidential user data, allowing unauthorized access by malicious actors.
Security analyst Noah Gregory from WTS.Dev has provided detailed insights into this vulnerability. He found that flaws in the macOS Keychain mechanism allow attackers to access stored passwords and sensitive data without user consent.
macOS Keychain is a built-in security feature designed to securely store passwords and confidential information. However, due to the identified vulnerability, unauthorized scripts can retrieve data under certain conditions.
Gregory and his team presented a Proof-of-Concept (PoC) exploit demonstrating how the vulnerability can be leveraged:
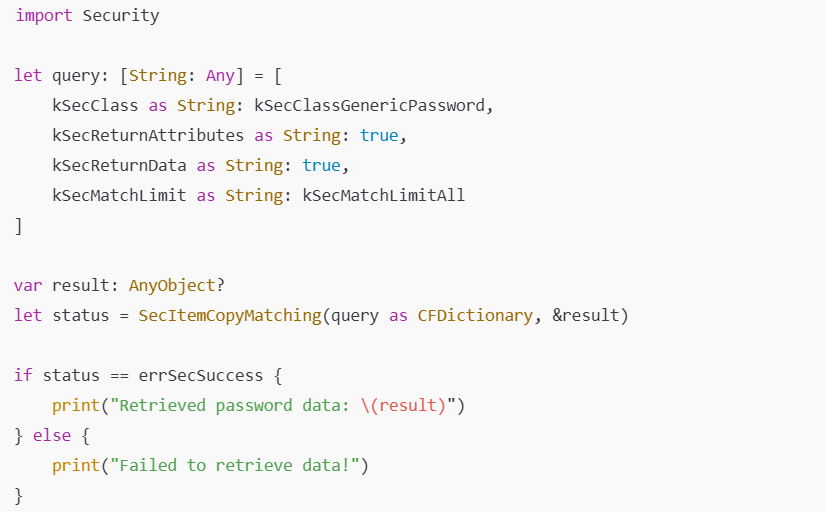
This code allows attackers to extract sensitive data from Keychain. Normally, macOS should restrict access to Keychain without proper authentication, but this flaw enables bypassing these security measures in certain scenarios.
Potential Risks of the Vulnerability
✅ Password leaks – If exploited, this vulnerability could lead to the theft of stored system passwords.
✅ Exposure of personal data – Keychain stores not only passwords but also credit card details, private documents, and user account credentials.
✅ Complete system compromise – Attackers could exploit this flaw to gain full access to macOS systems.
✅ Malicious app-based attacks – Hackers may create harmful applications that secretly request Keychain access.
How to Protect Yourself
Apple has acknowledged the vulnerability and is working on a security patch in upcoming macOS updates. Until an official fix is released, users should take the following security precautions:
🔹 Keep your system updated – Install Apple’s security updates as soon as they become available.
🔹 Avoid untrusted applications – Download apps only from the Mac App Store or reputable sources.
🔹 Use additional security software – Employ third-party security tools to prevent unauthorized access to Keychain.
🔹 Monitor app permissions – Regularly check which applications have access to Keychain and restrict unnecessary access.
This newly discovered macOS vulnerability poses a serious security risk, potentially leading to data breaches. While Apple works on a fix, users should take proactive steps to safeguard their information.
📌 Key Recommendations:
✅ Always keep macOS up to date
✅ Regularly review app permissions
✅ Avoid installing unknown software
✅ Use extra security tools for protection
Your system’s security is in your hands! 🔐



