Cybercriminals Exploit Fortinet Vulnerabilities to Launch SuperBlack Ransomware Attacks
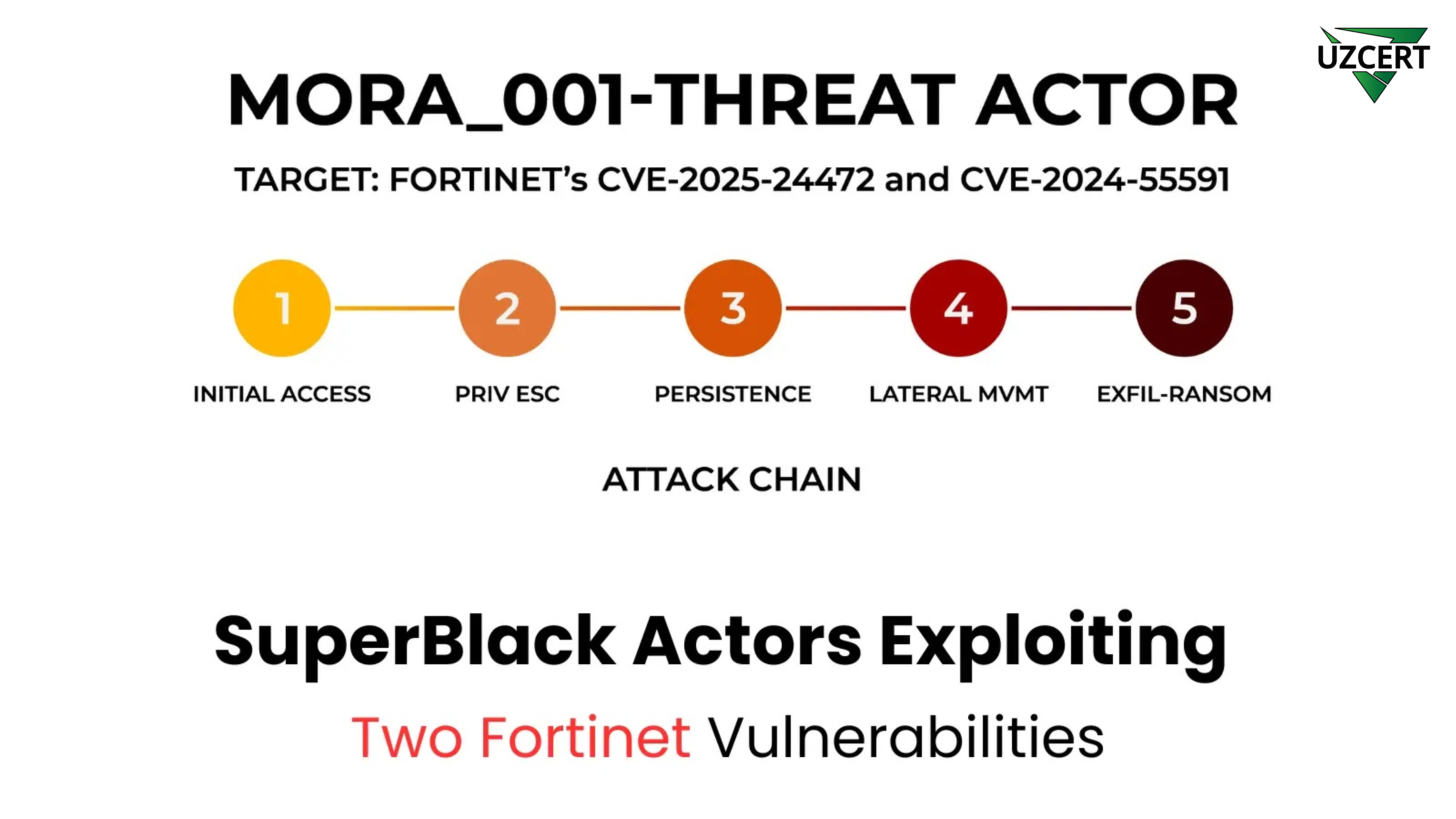
Between late January and early March 2025, cybersecurity researchers from Forescout’s Vedere Labs identified a series of sophisticated attacks conducted by a threat actor tracked as Mora_001. These attacks targeted Fortinet systems, exploiting vulnerabilities to deploy a specially crafted SuperBlack ransomware.
Mora_001 cybercriminals exploited CVE-2024-55591 and CVE-2025-24472, which affected FortiOS versions prior to 7.0.16. These vulnerabilities allowed attackers to gain super-admin privileges without authentication.
Researchers identified two primary exploitation methods:
🔹 Using a WebSocket vulnerability via the Jsconsole interface – attackers successfully spoofed IP addresses (127.0.0.1, 8.8.8.8, and others) to gain system access.
🔹 Using HTTPS requests – a direct method to bypass authentication and exploit the vulnerability.
Notably, these exploits were actively used within 96 hours of the PoC (proof-of-concept) being published publicly.
After successfully infiltrating the system, Mora_001 employed multiple sophisticated techniques to persist in the network:
✅ Creating new user accounts – accounts such as “forticloud-tech,” “fortigate-firewall,” “adnimistrator” (a misspelled version of “administrator”) were created with administrator privileges.
✅ Using automated scripts for persistence – attackers deployed scripts that executed daily, ensuring their accounts were automatically recreated even after system resets. For example, the user “forticloud-sync” was repeatedly generated with super-admin privileges.
✅ Spreading laterally across the network – if FortiGate devices operated in High Availability (HA) mode, attackers used configuration synchronization to gain access to additional systems.
✅ Conducting covert network reconnaissance – attackers scanned FortiGate management panels to identify weak points in the network.
✅ Using VPN for stealth access – new VPN accounts were created, closely resembling legitimate user accounts (e.g., xxx1).
Mora_001 used various methods to penetrate deeper into networks:
✔ VPN account access for deeper network infiltration
✔ HA configuration abuse to control other firewall devices
✔ Exploiting TACACS+ or RADIUS authentication infrastructure
✔ Executing remote commands via Windows Management Instrumentation (WMIC)
✔ Connecting to other servers and network devices via SSH
The attackers focused on critical network systems, including file servers, authentication servers, domain controllers, and databases.
First, the data was stolen, and then it was encrypted, following the double extortion model.
SuperBlack ransomware shares significant similarities with LockBit 3.0 (LockBit Black) but with certain modifications:
🔹 Ransom note structure was altered
🔹 A dedicated data exfiltration tool was added
🔹 LockBit elements were removed, but core system architecture remained intact
The ransom note contained a Tox ID (DED25DCB2AAAF65A05BEA584A0D1BB1D55DD2D8BB4185FA39B5175C60C8DDD0C0A7F8A8EC815), which was previously linked to LockBit 3.0.
According to available data, SuperBlack ransomware shares features with BlackMatter, LockBit, and BlackMatte, suggesting that it may have been built using a LockBit ransomware builder.
To prevent these attacks, it is essential to:
✔ Immediately update FortiOS to the latest version that patches CVE-2024-55591 and CVE-2025-24472
✔ Disable external administrative interfaces or restrict access
✔ Regularly review administrator accounts and remove suspicious users
✔ Analyze automated tasks (cron jobs, scripts) and eliminate unknown processes
✔ Monitor VPN accounts for unusual activity
✔ Continuously monitor network traffic and analyze HTTP/S, CLI, and authentication logs
The Mora_001 attacks have once again demonstrated that perimeter security devices like Fortinet can be exploited by cybercriminals to infiltrate networks.
This threat not only encrypts data but also steals it beforehand, increasing pressure on victims through a double extortion strategy.
Regular system updates, network monitoring, and proactive threat mitigation are critical defense measures. Otherwise, such advanced attacks could cause severe damage to IT infrastructure.



