
Critical Vulnerability in Splunk: Attackers Can Upload Malicious Files and Take Control of the System
🔍 Cybersecurity experts have discovered a serious vulnerability in the Splunk system. This flaw allows attackers to upload malicious files and execute arbitrary code within the system.
Splunk has identified a Remote Code Execution (RCE) vulnerability, CVE-2025-20229, in its Splunk Enterprise and Splunk Cloud Platform products. This vulnerability enables low-privileged users to upload malicious files into the system and execute arbitrary commands.
How Does It Work?
- The vulnerability exists in older versions of Splunk Enterprise and unpatched Splunk Cloud Platform systems.
- An attacker can upload a specially crafted file to the $SPLUNK_HOME/var/run/splunk/apptemp directory to bypass authentication checks.
- This allows unauthorized access and potential full system control.
Splunk has assessed this vulnerability as highly critical, assigning it a CVSSv3.1 score of 8.0.
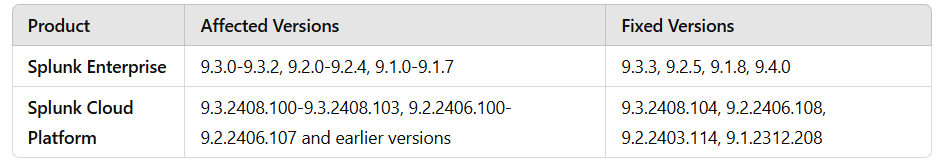
🔴 The following versions are vulnerable:
Additionally, another security flaw (CVE-2025-20231) has been identified in the Splunk Secure Gateway application.
What Is the Risk?
- An attacker can use a low-privileged account to send requests on behalf of a higher-privileged user.
- This can lead to unauthorized access to confidential data.
- The vulnerability stems from session data and authentication tokens being stored in plain text within the splunk_secure_gateway.log file.
This vulnerability also poses a high security risk, with a CVSSv3.1 score of 7.1.
🔹 What Should Splunk Enterprise Users Do?
✅ Update the System:
- Splunk Enterprise users must update their system to one of the following versions:
- 9.4.0, 9.3.3, 9.2.5, 9.1.8, or later.
- Splunk Cloud Platform users should wait for the automatic update provided by Splunk.
✅ Additional Security Measures:
- Restrict non-administrator users.
- Monitor and restrict file uploads.
- Use IDS/IPS security systems.
🔹 What Should Splunk Secure Gateway Users Do?
✅ Update the Application:
- Upgrade Splunk Secure Gateway to version 3.8.38 or 3.7.23.
✅ Temporary Mitigation Measures:
- Temporarily disable the Splunk Secure Gateway application (this may impact Splunk Mobile, Spacebridge, and Mission Control users).
The CVE-2025-20229 and CVE-2025-20231 vulnerabilities pose a serious threat to Splunk users. Attackers can exploit these flaws to execute malicious code and gain unauthorized access to sensitive data.
For this reason, Splunk users must apply the necessary updates immediately and implement additional security measures. Cybercriminals are always searching for new vulnerabilities, making regular system updates essential. 🚨
📢 Reminder: The fundamental principle of cybersecurity is prevention and rapid response to threats!



