
Critical Vulnerability in Apache Roller: Hackers Remain in the System Even After Password Changes
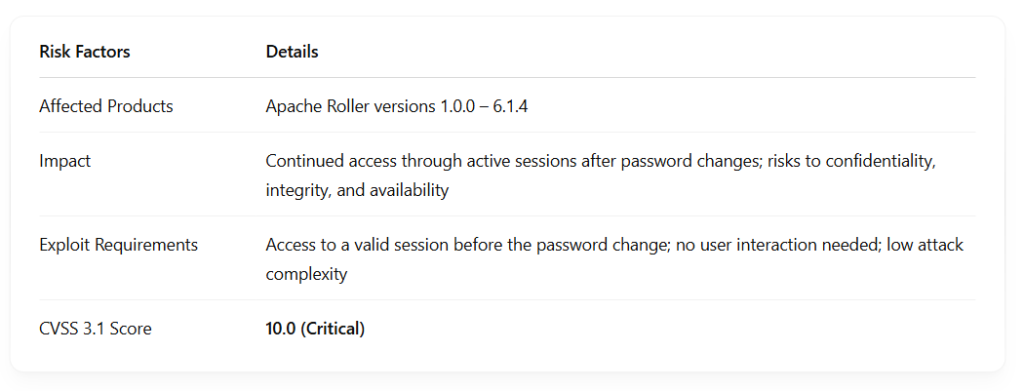
A dangerous vulnerability discovered in the popular blogging platform Apache Roller poses a serious threat to users and organizations. The vulnerability, identified as CVE-2025-24859, affects all versions of the platform from 1.0.0 to 6.1.4 and has received the highest CVSS 4.0 rating — 10.0, indicating maximum severity.
The root of the issue lies in Apache Roller’s flawed session management system. When a user or administrator changes an account password, the system fails to terminate any previously active sessions. This means that if a hacker had already gained access, they could continue operating within the system even after the password has been changed.
The vulnerability was discovered by cybersecurity researcher Haining Meng and stems from the platform’s decentralized session management architecture. As a result, active sessions operate independently and do not respond to changes in authentication status, leaving systems vulnerable to persistent unauthorized access.
Summary of the Vulnerability:
In cybersecurity, the standard first response to a suspected password compromise is to change the password immediately. However, in vulnerable versions of Apache Roller, changing the password provides no protection — attackers with existing sessions can maintain full access and continue their activities.
Apache Roller is a Java EE-based, multi-user blogging platform widely used both for personal blogs and by organizations. Its broad user base makes the potential impact of this vulnerability even more serious.
The Fix
The Apache Software Foundation addressed the issue in version 6.1.5, which implements centralized session management. With this fix, all active sessions are now automatically terminated when a password is changed or a user account is disabled.
Recommendations for organizations unable to update immediately:
- Closely monitor system logs and review session activity;
- Implement network-level protections (such as allowing access only from trusted IP addresses);
- If sensitive data is stored within the system, consider temporarily disabling the application.
Past vulnerabilities in Apache Roller:
This is not the first major security issue affecting Apache Roller. Previously reported vulnerabilities include:
- CVE-2013-4212 — Remote code execution via OGNL injection;
- CVE-2014-0030 — File disclosure through XML External Entity (XXE) injection.
Conclusion:
Users of Apache Roller must take this vulnerability seriously. Timely updates are one of the most important pillars of modern cybersecurity. In cases where sensitive personal or organizational information is at risk, vulnerabilities like this could lead to irreversible damage.



