
🔐 Critical Vulnerability Discovered in ASUS Servers
Recent security analyses have identified a severe vulnerability, CVE-2024-54085, posing a significant threat to server infrastructure. This vulnerability resides in the MegaRAC BMC (Baseboard Management Controller) firmware developed by AMI, widely used by major server manufacturers such as ASUS, Lenovo, HPE, and ASRock.
Vulnerability Details:
- Vulnerability ID: CVE-2024-54085
- Severity Rating (CVSS v4): 10.0 (Critical)
- Affected Manufacturers: ASUS, Lenovo, HPE, ASRock, and others
- Affected Module: MegaRAC BMC (Baseboard Management Controller)
- External Interface: Redfish API – a protocol for remote server management over networks
If successfully exploited, this vulnerability could allow hackers to gain full control over the server, either locally or remotely. Potential malicious actions include:
- Installing ransomware or other persistent malware
- Manipulating firmware at the firmware level (firmware-level tampering)
- Damaging server components through over-voltage
- Forcing the system into an endless reboot loop
- Causing complete hardware failure due to critical component damage
Such incidents could result in substantial financial losses, system downtime, and the loss of sensitive data for enterprises and organizations.
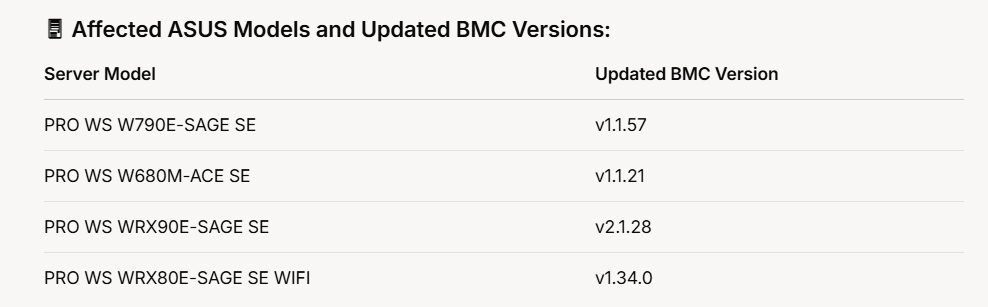
Note: ASUS users are urged to immediately update their BMC firmware to the versions listed above.
✅ Lenovo and HPE Have Already Released Patches
The good news is that Lenovo and HPE have already released security patches to address this vulnerability. These updates enable users and IT professionals to restore security promptly without additional delays.
📣 Recommendations for Organizations
- Notify Stakeholders: Immediately inform shareholders, subsidiaries, and technology partners about this vulnerability.
- Update BMC Firmware: Schedule urgent updates for BMC firmware.
- Enhance Monitoring: Strengthen network monitoring of the Redfish interface used by servers.
- Restrict Access: Disable remote management ports (IPMI, Redfish, SSH, etc.) if not in use, or restrict access to VPN-only connections.
- Comprehensive Scanning: Conduct a full security scan of all servers in the system using appropriate tools.
The United Arab Emirates Cybersecurity Council expresses gratitude to all partners and encourages sharing any updates, detected incidents, or technical details related to this vulnerability.
In today’s world, cybersecurity is not just a technological issue but a critical strategic priority built on mutual trust, transparency, and collaboration.



