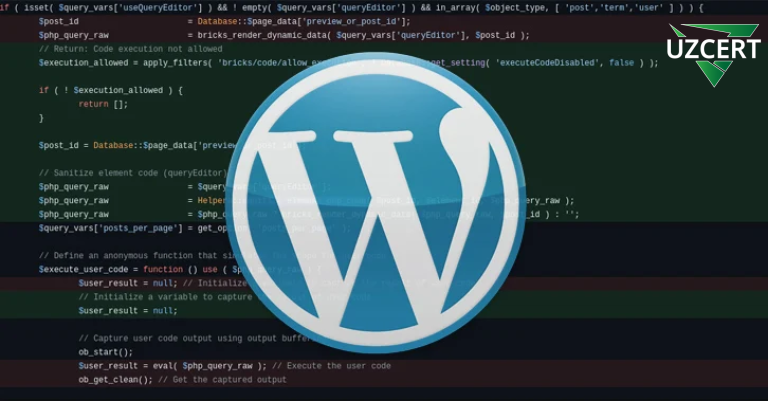
Intezer: A User-Friendly Tool for Threat Detection and Analysis
In today’s world, technology has become an integral part of our lives, but with it comes increased risks. This is why cybersecurity has become essential, requiring various tools to detect threats and protect systems. Intezer Analyze is one such tool…