BitM: A New Cyber Threat That Steals Confidential Data via Browsers
In recent years, cybercriminals have been mastering innovative techniques to bypass security systems. One such method is BitM (Browser-in-the-Middle), a new attack tactic that allows hackers to hijack user sessions within seconds and gain access to their systems.
What makes BitM even more dangerous is its ability to bypass Multi-Factor Authentication (MFA), rendering the final line of defense ineffective for many organizations.
🔹 How Does a BitM Attack Work?
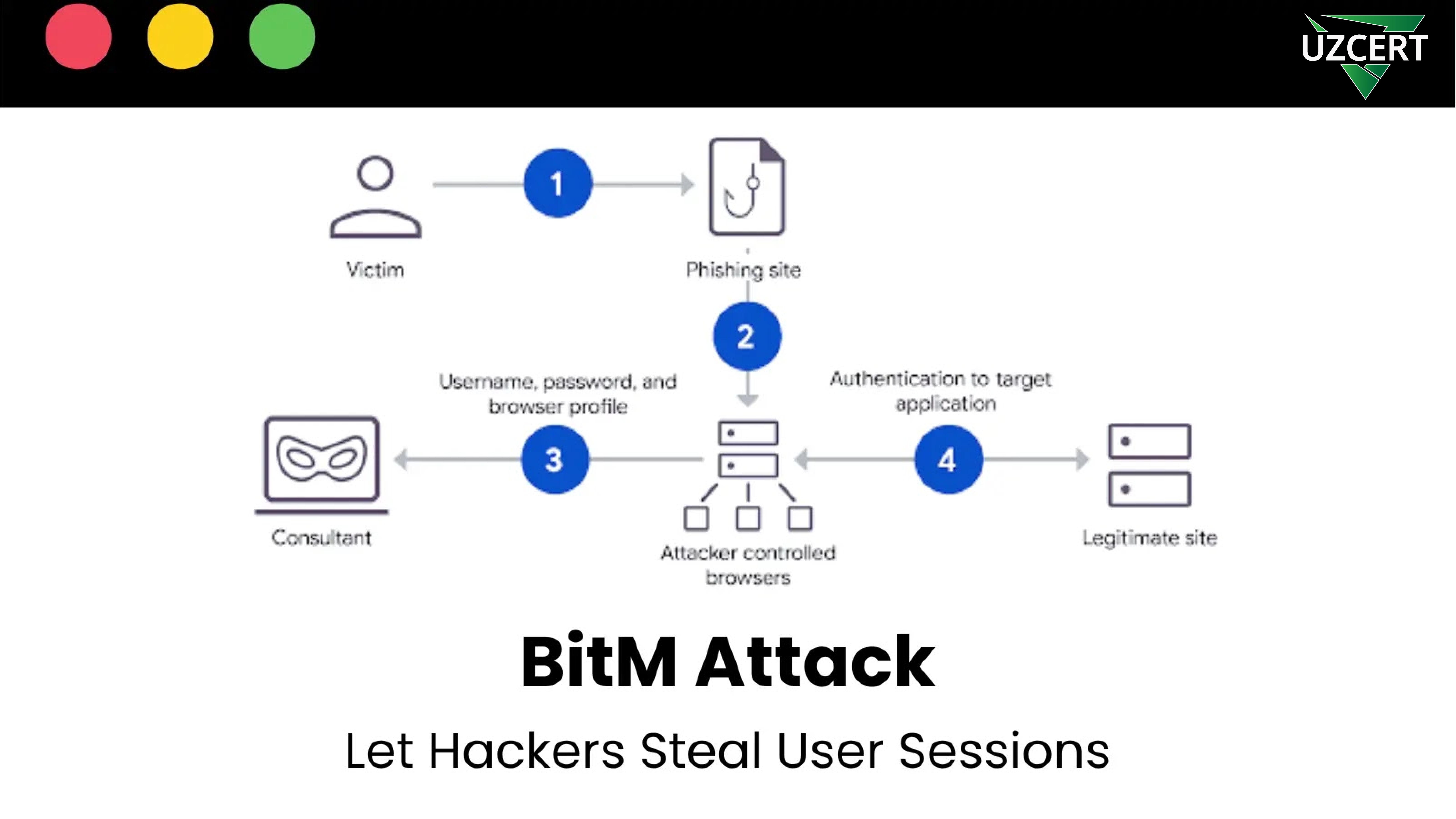
BitM attacks occur directly in the user’s browser. Hackers intercept session tokens, allowing them to log in as the victim without needing their credentials again. Attackers achieve this through the following methods:
1. Browser Proxying
Hackers force the victim to use a special proxy browser controlled by them. This is done through:
✔ Phishing links – The victim clicks a malicious link and is redirected to an attacker-controlled page.
✔ Hidden proxy systems – The victim believes they are accessing a legitimate website, but in reality, they are interacting with a fake page through a proxy browser.
The fake website appears identical to the real one, and when the user enters their credentials and even completes MFA, the attackers intercept the session token.
2. Session Token Hijacking
BitM attacks completely nullify MFA security because once an attacker steals a session token, they no longer need to request a password or authentication codes. With the stolen token, they can log in at any time without the user’s knowledge.
⚠ Which Systems Are Most Vulnerable?
✔ Enterprise networks – BitM allows hackers to access Active Directory, databases, and internal systems.
✔ Cloud services (Google, Microsoft 365, AWS, etc.) – Since cloud platforms rely heavily on session tokens, BitM attacks are particularly dangerous for them.
✔ Virtual Desktop Infrastructures (VDI) – Attackers can use stolen session tokens to access remote work environments and infiltrate corporate networks.
🔹 Tools Used by Hackers
🔸 Evilginx2 – A well-known phishing tool for hijacking session tokens.
🔸 Delusion – An advanced BitM attack tool developed by Mandiant that allows real-time session monitoring and automated attack scaling.
🔸 Firefox Profile Theft – Attackers copy the victim’s browser profile to reuse stored session tokens later.
🔴 Why Are BitM Attacks So Dangerous?
✔ Lightning-fast execution – Attackers can gain full access within seconds.
✔ Highly scalable – BitM attacks can simultaneously target thousands of users.
✔ MFA becomes useless – Hackers steal session tokens, enabling persistent access without the victim noticing.
✅ How to Protect Against BitM Attacks?
✔ Use FIDO2 Security Keys (YubiKey, Google Titan, etc.)
These cryptographic authentication keys generate responses that are domain-specific, making BitM attacks nearly impossible since hackers cannot transfer the authentication data to another site.
✔ Implement Client Certificates
Binding authentication to a specific device ensures that attackers cannot reuse a stolen session on a different machine.
✔ Monitor Browser Behavior
Detection tools should check for:
✔ Browser fingerprinting mismatches.
✔ Unusual session activity.
✔ Suspicious browser agent usage.
✔ Train Employees on Cybersecurity Awareness
Organizations should educate users on:
✔ Identifying suspicious URLs before entering credentials.
✔ Being cautious of unexpected MFA requests.
✔ Recognizing unusual browser session behavior.
🚨 Conclusion
BitM attacks represent a new frontier in cyber threats, allowing attackers to hijack user sessions directly in the browser. To effectively combat these attacks, companies must adopt FIDO2 security keys, client certificates, and advanced behavioral monitoring systems.
💡 Remember: Any system can be vulnerable, but with the right security measures, even sophisticated attacks like BitM can be prevented!



