
A Critical Vulnerability Threatens WordPress Sites!
Cybersecurity researchers have discovered a critical vulnerability in the popular WordPress plugin — InstaWP Connect. This vulnerability could potentially expose thousands of websites to remote attacks.
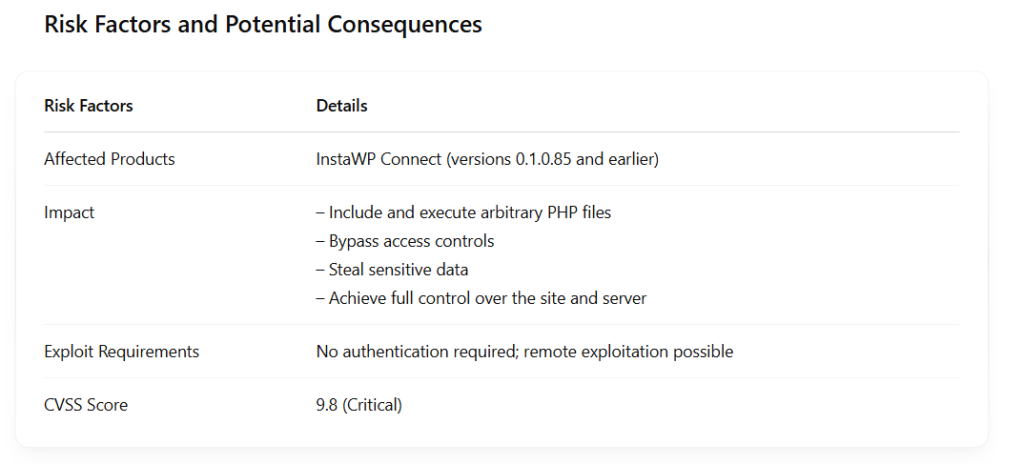
Experts from Wordfence identified and reported the vulnerability CVE-2025-2636, which allows unauthenticated attackers to execute arbitrary code on a vulnerable website’s server.
This vulnerability received the highest possible CVSS score — 9.8 out of 10.
The vulnerability affects all versions of the InstaWP Connect plugin up to and including version 0.1.0.85.
This flaw is related to Local File Inclusion (LFI) — a technique that allows attackers to include files stored on the server. The root of the problem is that the plugin fails to properly validate user input and directly passes it to PHP functions.
The vulnerability can be exploited through the instawp-database-manager parameter. Using a specially crafted HTTP request, an attacker can include and execute any file on the server.
Recommendations for Website Owners
- All users of the InstaWP Connect plugin are strongly advised to immediately update to version 0.1.0.86 or newer.
- If updating is not possible right away, temporarily deactivate the plugin until a patch is applied.
- It is also recommended to use a Web Application Firewall (WAF) as an additional security layer.
- Regularly update all plugins and components on your website.
This vulnerability is considered one of the most dangerous for WordPress users. What makes it particularly alarming is that an attacker can exploit it remotely, without any authentication, using just a simple HTTP request.
Failure to update plugins on time and neglecting cybersecurity measures may result in a complete compromise of the website and loss of control over the server.
Therefore, WordPress site owners are strongly advised to always stay vigilant, update plugins regularly, and implement essential cybersecurity measures to protect their websites!



