
Vulnerabilities in Adobe Acrobat Reader Put User Data at Risk
Adobe Acrobat Reader, an essential tool for document exchange and official paperwork, has been found to contain three critical vulnerabilities. These flaws could allow attackers to execute arbitrary code or disclose sensitive information.
The vulnerabilities were discovered by Cisco Talos security researchers and could open new attack vectors for cyber threats via PDF documents. If a user opens a specially crafted malicious PDF file, an attacker could exploit these weaknesses to gain access to the system and perform various harmful actions.
Let’s examine the details of these vulnerabilities.
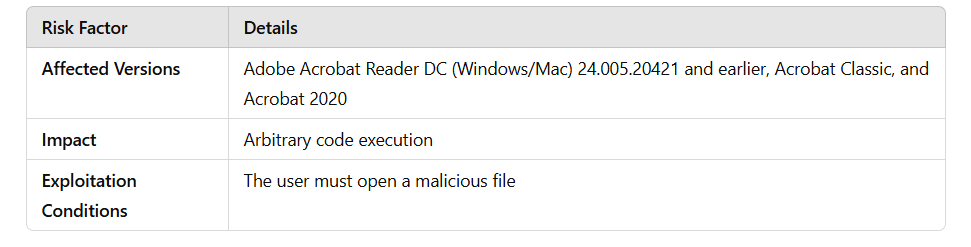
1. Memory Corruption Vulnerability – CVE-2025-27158
This vulnerability arises due to improper memory management in Adobe Acrobat Reader’s font processing mechanism. The issue occurs because the software uses an uninitialized pointer.
🔴 Severity Level: High (CVSS 3.1: 8.8)
🎯 How Does the Attack Work?
1️⃣ The attacker creates a malicious PDF file containing a specially crafted font.
2️⃣ When the user opens the file, memory corruption occurs during font processing.
3️⃣ This enables the attacker to execute arbitrary code.
🛑 Potential Impact:
✔ Installation of malware.
✔ Modification or deletion of critical files using user privileges.
✔ Silent theft of confidential data.
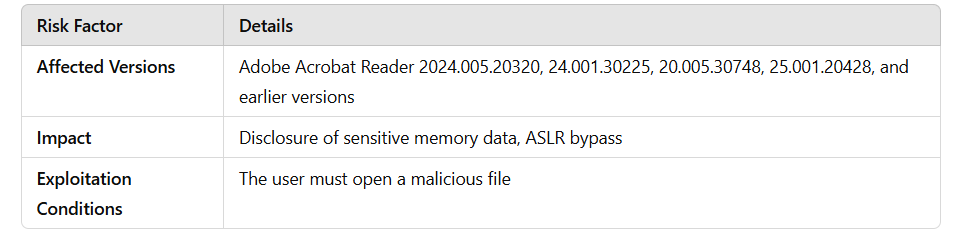
2. Out-of-Bounds Read Vulnerability – CVE-2025-27163
This vulnerability is caused by an error in Adobe Acrobat Reader’s handling of OpenType fonts. The software may incorrectly process hhea and hmtx tables, potentially leading to memory leaks.
🟡 Severity Level: Medium (CVSS 3.1: 6.5)
🎯 How Does the Attack Work?
1️⃣ The attacker prepares a PDF file with a specially crafted font.
2️⃣ When the user opens the document, the software reads more data from memory than intended.
3️⃣ This could allow the attacker to retrieve sensitive data such as passwords or encryption keys.
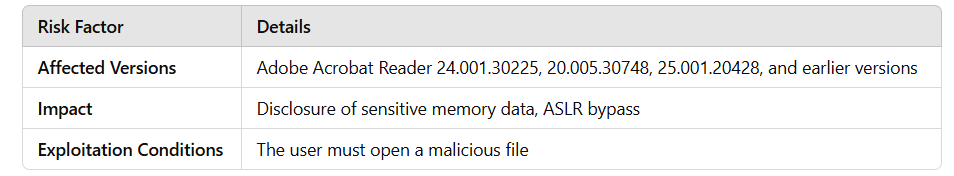
3. Out-of-Bounds Read Vulnerability – CVE-2025-27164
This vulnerability, similar to the previous one, occurs during the processing of OpenType fonts and falls under the CWE-125 (Out-of-Bounds Read) category.
🟡 Severity Level: Medium (CVSS 3.1: 6.5)
Security Measures and Recommendations
🔹 Immediately update Adobe Acrobat Reader to the latest version. Patches for these vulnerabilities were released on March 11, 2025.
🔹 Enable automatic updates to ensure users receive the latest security fixes.
🔹 Implement network monitoring and update Snort rules to detect attempts to exploit these vulnerabilities.
🔹 Be cautious with emails and PDF documents from unknown sources.
🔹 Enterprise users should enable EPP (Endpoint Protection Platform) and EDR (Endpoint Detection and Response) solutions to monitor and prevent attacks.
The newly discovered vulnerabilities in Adobe Acrobat Reader pose a significant threat to users and organizations. Attackers can exploit these weaknesses to execute arbitrary code, leak memory data, and compromise system security.
Taking appropriate security measures and applying updates promptly can help mitigate these risks. Every user should stay vigilant and handle suspicious documents with caution. 🚨



