
New Security Vulnerabilities in GitLab Allow Authentication Bypass and Remote Code Execution
GitLab has alerted its users to critical security vulnerabilities and urged them to update their systems immediately. According to the latest security update, attackers could exploit these vulnerabilities to access the system as legitimate users or execute arbitrary code within the GitLab environment.
Security analysis has identified two major security issues in GitLab:
- Critical authentication bypass vulnerabilities (CVE-2025-25291 and CVE-2025-25292).
- Remote code execution vulnerability (CVE-2025-27407).
These vulnerabilities are linked to SAML Single Sign-On (SSO) authentication and the GraphQL library used in GitLab.
1. Authentication Bypass Vulnerabilities
The vulnerabilities CVE-2025-25291 and CVE-2025-25292 were discovered in the ruby-saml library, which is used for SAML SSO authentication in GitLab. The risk associated with these vulnerabilities is that if an attacker possesses a validly signed SAML document, they could exploit the flaw to log in as another user.
Impact Scope
- Affected systems: GitLab Community Edition (CE) and Enterprise Edition (EE).
- Vulnerable libraries: ruby-saml versions 1.13.0 to 1.18.0 and versions older than 1.12.4.
- Risk level: Critical.
- Attack conditions: The attacker must have a signed SAML document.
2. Remote Code Execution Vulnerability
The vulnerability CVE-2025-27407 was found in the Ruby GraphQL library used in GitLab. By exploiting this flaw, an attacker with GitLab authentication could transfer a malicious project to another account and execute arbitrary code within the GitLab environment.
Impact Scope
- Affected systems: GitLab CE/EE.
- Risk level: High.
- Attack conditions: The attacker must be a authenticated GitLab user.
Importantly, this vulnerability is linked to the Direct Transfer feature. Currently, this feature is in beta and disabled by default, meaning users who have not enabled it are not affected by the security risk.
PostgreSQL Updates and System Optimization
Alongside these security patches, GitLab has also announced an update to PostgreSQL versions 14.17 and 16.8. These updates address several issues:
- Delays in search functionality caused by special characters.
- Errors occurring within project repositories.
- Overall system component optimizations.
How to Protect Your System?
GitLab strongly recommends users take the following steps to secure their systems:
1. Update GitLab Immediately
Upgrade GitLab to one of the latest patched versions:
- 17.9.2, 17.8.5, or 17.7.7.
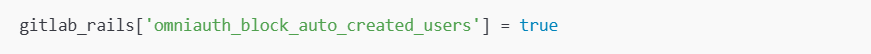
2. Enhance SAML Authentication Security
- Enable GitLab Two-Factor Authentication (2FA).
- Disable the SAML two-factor authentication bypass feature.
- Require administrator approval for newly created users: rubyКопироватьРедактировать
3. Keep Direct Transfer Disabled
If this feature is enabled, disable it immediately.
4. Follow Official Security Recommendations
GitLab regularly publishes security updates on its official website. The latest security advisories can be found here.
The newly discovered vulnerabilities in GitLab could allow attackers to bypass user authentication and gain privileged access to the system. Therefore, it is critical to update all self-managed GitLab instances immediately. This is especially important for organizations using SAML authentication or considering enabling the Direct Transfer feature.
To ensure your system’s security, stay updated with GitLab’s official patches and follow the recommended security measures!



