Chinese Hackers Compromise Juniper Routers and Use Them for Espionage
In today’s world, one of the most serious cybersecurity threats is attacks targeting network infrastructure. In mid-2024, researchers discovered that Juniper Networks’ Junos OS contained backdoors that allowed attackers to gain hidden access. This attack was carried out by the state-sponsored espionage group UNC3886, which is linked to China.
This incident poses a significant threat to telecommunications and national security, especially since the targets were outdated and unsupported devices.
🔍 Attack Details: Who, How, and Which Devices Were Targeted?
🔴 Which devices were attacked? Juniper Networks MX-series routers.
🔴 Why were they targeted? These devices had outdated hardware and software, making them vulnerable to modern exploits.
🔴 Who carried out the attack? The Chinese-affiliated hacking group UNC3886.
🔴 How did they gain access? Hackers used valid credentials to obtain high-level system privileges.
According to security researchers at Google Mandiant, multiple backdoor malware variants based on TINYSHELL were found on the compromised routers. Their primary purpose was to maintain long-term hidden access, evade detection, and steal confidential information.
🛑 Most Dangerous Exploits and Vulnerabilities
One of the most alarming aspects of this attack was that UNC3886 hackers bypassed Juniper Networks’ security mechanisms. They exploited the CVE-2025-21590 vulnerability, which allowed them to bypass Juniper’s Verified Exec (veriexec) security system.
Veriexec is a kernel-level file integrity verification system designed to prevent unauthorized code execution. However, hackers managed to circumvent this protection and inject malicious code into the Junos OS operating system.
🔬 Malware Variants and Their Capabilities
The hackers modified the open-source TINYSHELL malware to create a custom backdoor tailored for Junos OS. The most dangerous variants include:
1️⃣ “appid” – Established encrypted communication with servers at TCP://129.126.109.50:22 and TCP://116.88.34.184:22, using AES encryption to secretly transmit and manage malicious payloads.
2️⃣ “lmpad” – Deleted log files to erase traces of hacker activity. It executed the following commands:
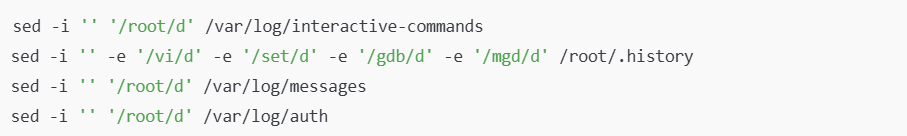
These actions allowed attackers to remain undetected by erasing records of their operations from system logs.
3️⃣ Other malicious commands included:
tshd_get_file– Uploading files to a remote servertshd_put_file– Downloading files from a remote servertshd_runshell– Running a/bin/shshell sessiontshd_setproxy– Setting up a Socks proxy for a specific IP and porttshd_config– Modifying system configurations
This attack highlights the increasing sophistication of cyber espionage operations targeting network infrastructure. Since Juniper MX routers are widely used in corporate and government networks, their compromise could lead to severe data breaches.
The backdoors gave hackers the ability to:
✅ Maintain persistent access to confidential corporate and government data
✅ Intercept network traffic and decrypt encrypted communications
✅ Use compromised routers as proxy servers to spread additional malware
In the worst-case scenario, this threat could impact international telecommunications networks or result in the theft of classified government data.
🔐 Security Recommendations
✅ 1. Update Juniper Devices Immediately!
Juniper Networks has released patches to address these vulnerabilities. It is recommended to upgrade to Junos OS 6.2.0 or a later version.
✅ 2. Enable Network Monitoring!
Monitor logs for unusual activities, particularly:
- Sudden privilege escalation to administrator level
- Suspicious outbound traffic routed through proxies
- Encrypted connections to unknown IP addresses
✅ 3. Audit User Accounts and Authentication!
To prevent unauthorized access:
- Remove unnecessary user accounts
- Enable two-factor authentication (2FA)
- Restrict router access to VPN connections only
✅ 4. Special Recommendations for Governments and Large Enterprises
If your organization relies on Juniper devices:
- Strengthen network segmentation
- Deploy Intrusion Detection/Prevention Systems (IDS/IPS)
- Secure communications using VPNs and encryption
This incident once again proves that outdated devices and weak cybersecurity practices create severe risks for network security. If Juniper Networks routers are not updated and secured, the consequences could be catastrophic! 🚨