
GitHub Copilot: A New Approach to Log Analysis for Cybersecurity Professionals
In the modern field of cybersecurity, analyzing system logs plays a crucial role. Automated log processing has become essential for detecting cyberattacks, responding to incidents promptly, and ensuring data protection.
GitHub has taken its AI-powered coding assistant Copilot to the next level by tailoring it specifically for cybersecurity professionals to analyze logs, identify anomalies, and accelerate threat response.
Let’s explore how this tool works, its advantages, and future development prospects.
A New Approach to Log Analysis with GitHub Copilot
Modern Security Operations Centers (SOC) process thousands of logs per second. Firewalls, Intrusion Detection Systems (IDS), endpoint protection platforms, and SIEM systems generate vast amounts of data.
GitHub Copilot simplifies this process in three key ways:
1. Automated Log Processing
Copilot allows security specialists to quickly create Python scripts for automated log processing.
Example: analyzing AWS CloudTrail logs, generated by Copilot:
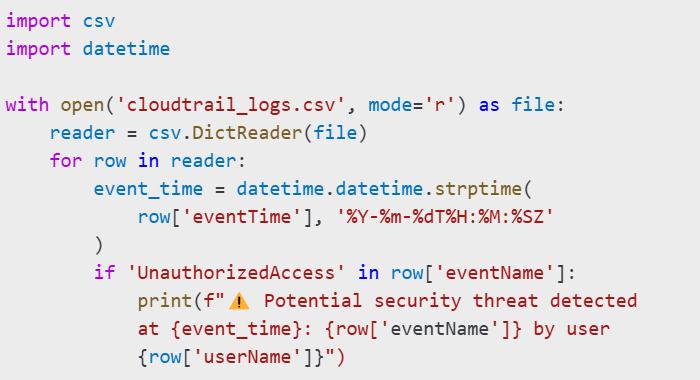
This code automatically identifies unauthorized access attempts or potentially malicious actions.
2. Anomaly Detection with AI
GitHub Copilot can analyze attack patterns. For instance, if multiple failed login attempts are recorded, the tool will suggest the following actions:
🔍 Attack Indicators:
“Three failed login attempts for an admin account from the same IP address within four seconds. Possible brute-force attack.”
✅ Recommended Actions: ✔ Block the IP address in the firewall. ✔ Review account lockout policy. ✔ Analyze authentication logs for broader attack patterns.
3. Command Line (CLI) Optimization
Many security professionals work with Linux audit logs. Copilot integrates with command-line tools, speeding up log analysis.
Example: Finding failed root login attempts via SSH

Copilot enhances such commands by automatically generating scripts using awk, sed, and jq for processing JSON-formatted logs.
GitHub Copilot places a strong emphasis on security and offers specialized features for corporate environments:
🔹 Security-Aware Code Suggestions – Copilot checks code against OWASP Top 10 and CIS Benchmarks.
🔹 Automated Data Anonymization – Copilot supports PII (Personally Identifiable Information) redaction in log processing.
🔹 SIEM Integration – Pre-configured connectors are available for Splunk, ELK Stack, and Azure Sentinel.
Example: FinTech Corp achieved a 68% reduction in phishing attack detection time using Copilot-generated log correlation rules.
GitHub has announced further enhancements for Copilot:
🚀 Real-time Log Analysis – Monitoring events as they happen. 🚀 Automated MITRE ATT&CK Mapping – Linking attacks to MITRE tactics and techniques. 🚀 Threat Intelligence Enrichment – Integrating real-time threat intelligence sources. 🚀 Collaborative Incident Analysis – Enabling multiple security specialists to analyze logs together.
GitHub Copilot continuously learns from millions of repositories, adapting to new threats and attack techniques.
🔹 GitHub Copilot is becoming a powerful tool not only for developers, but also for security professionals.
🔹 AI accelerates log analysis, develops effective responses to cyberattacks, and creates automated security solutions.
🔹 Recommended for:
✔ Large enterprises – Implement automated log analysis with GitHub Copilot.
✔ SOC professionals – Strengthen threat detection mechanisms with AI.
✔ DevSecOps teams – Integrate Copilot to strengthen code review and security controls.
GitHub Copilot for Business ($19/user/month) is SOC 2 Type II certified, making it a reliable AI assistant for large enterprises and security professionals. 🚀



