
BadBox Malware Threatens Over 50,000 Android Devices
In today’s world, cyber threats are becoming increasingly sophisticated, and the risks to the Android ecosystem continue to rise. The BadBox 2.0 operation, discovered by the Satori Threat Intelligence team at HUMAN Security, is a prime example of this. By distributing 24 infected applications through Google Play, cybercriminals have compromised over 50,000 Android devices. This campaign is an expanded version of the original BadBox threat, which was exposed in 2023, but with more advanced hacking techniques.
The BadBox malware primarily targets budget-friendly devices from lesser-known brands that run on the Android Open Source Project (AOSP) platform, including:
📌 TV boxes
📌 Tablets
📌 Digital projectors
📌 Automotive multimedia systems
During their investigation, researchers identified a backdoor named BB2DOOR, which granted cybercriminals long-term privileged access to infected devices.
Experts at HUMAN Security discovered that four cybercriminal groups were behind this attack:
🔹 SalesTracker Group
🔹 MoYu Group
🔹 Lemon Group
🔹 LongTV
These groups collaborated to execute fraudulent schemes, including:
🔸 Illicit traffic redirection via proxy services
🔸 Click fraud and advertising scams
🔸 Stealth advertising mechanisms for financial gain
Infected devices downloaded a malicious library called libanl.so, which performed the following actions:
📌 Downloading additional malware files
📌 Connecting to command and control (C2) servers
📌 Activating hidden advertising mechanisms
Researchers analyzed the following code snippet to understand how the malware was triggered:
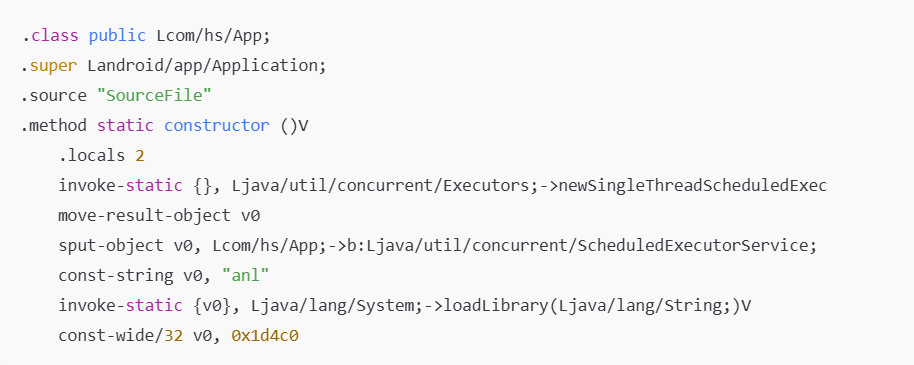
How Did Google Respond to the BadBox Threat?
✔ Strengthened Google Play Protect – malicious apps with similar characteristics are now automatically blocked, and users receive real-time warnings.
✔ Blocked fraudulent accounts – all developer accounts linked to BadBox 2.0 have been permanently banned from Google’s advertising ecosystem.
✔ Continuous app scanning – applications in the Play Store are routinely analyzed to ensure security.
How to Protect Yourself from BadBox?
🛡 Check if Google Play Protect is enabled – make sure Google Play Protect is turned on for your device.
🛡 Download apps only from official sources – installing applications from unknown sources significantly increases the risk of infection.
🛡 Verify your device’s Play Protect certification – all infected devices were found to be uncertified AOSP devices that lacked Google Play Protect verification.
🛡 Uninstall suspicious applications – if you have unknown or untrusted apps, remove them immediately.
🛡 Use VPNs and firewalls – protect your network connection using a reliable VPN service and firewall tools.
BadBox 2.0 is a large-scale and sophisticated cybercriminal operation that primarily targets low-cost Android devices, threatening users’ personal data and security. While Google has taken steps to mitigate the risk, users must remain vigilant and proactive in protecting their devices.
👀 Stay alert and safeguard your Android device against malware! 🚀



