
Palo Alto, Cisco, and Microsoft Exchange at Risk Due to 23 Vulnerabilities Exploited by the Black Basta Hacking Group
In recent days, one of the most alarming developments in cybersecurity has been the disclosure of internal chats from the Black Basta hacking group. Analysts at GreyNoise examined the leaked data and confirmed that out of 62 identified vulnerabilities, 23 are actively being exploited at this moment.
These vulnerabilities affect corporate network systems, security appliances, and widely used web applications, including Palo Alto PAN-OS, Cisco IOS, and Microsoft Exchange. The most concerning issue is that some of these exploited vulnerabilities have not yet been listed in CISA’s “Known Exploited Vulnerabilities” (KEV) catalog, emphasizing the urgent need for organizations to enhance their cybersecurity measures.
🔍 Targeted Systems:
Corporate Networks and Security Systems:
- Palo Alto PAN-OS (CVE-2024-3400)
- Cisco IOS XE (CVE-2023-20198)
- Juniper Junos OS (CVE-2023-36845, CVE-2023-36844)
Server Applications and Web Services:
- Microsoft Exchange (CVE-2022-41082, CVE-2021-26855)
- Atlassian Confluence (CVE-2023-22515, CVE-2022-26134)
- Zimbra Collaboration Suite (CVE-2022-37042, CVE-2022-27925)
Web Platforms and Plugins:
- WordPress Post SMTP Mailer (CVE-2023-6875)
- JetBrains TeamCity (CVE-2024-27198, CVE-2023-42793)
These vulnerabilities enable hackers to bypass authentication, execute remote code (RCE), steal confidential data, and gain deep access to corporate networks.
📊 Vulnerabilities Confirmed by GreyNoise in the Last 24 Hours:
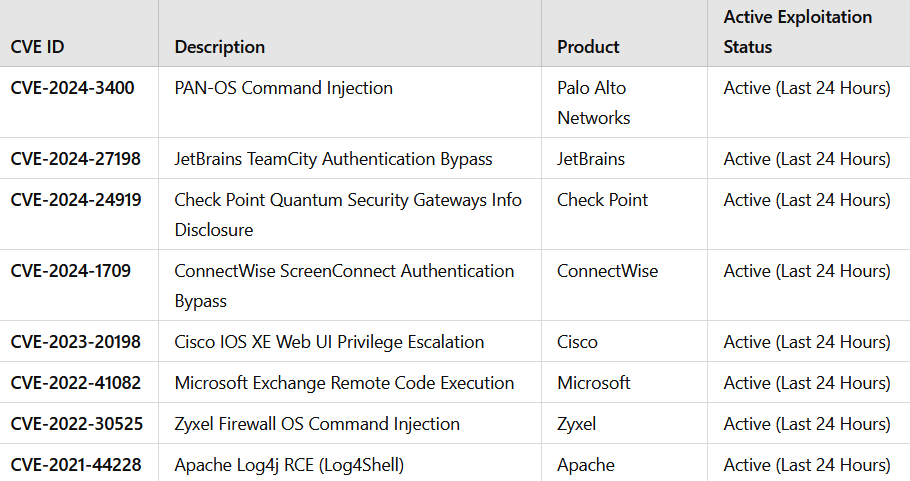
⚠ Black Basta’s Attack Techniques:
🔴 Authentication Bypass – Exploiting TeamCity (CVE-2024-27198) and ConnectWise ScreenConnect (CVE-2024-1709) to gain unauthorized access to systems without credentials.
🔴 Remote Code Execution (RCE) – Deploying malicious payloads through PAN-OS (CVE-2024-3400) and Microsoft Exchange (CVE-2022-41082) vulnerabilities.
🔴 Confidential Data Theft – Leveraging Citrix NetScaler ADC (CVE-2023-4966) and Check Point Quantum Security Gateways (CVE-2024-24919) to extract corporate information.
🛡 How to Defend Against These Attacks?
To mitigate cybersecurity risks, GreyNoise recommends the following essential security measures:
✅ Regular System Updates – Ensure all security patches released by Cisco, Microsoft, Palo Alto, Juniper, and other vendors are promptly applied.
✅ Isolation of Public-Facing Services – Exchange servers, VPN gateways, and Cisco IOS systems should not be directly accessible from the internet to minimize exposure.
✅ Enhanced Network Monitoring – Utilize security platforms like GreyNoise for real-time monitoring of actively exploited vulnerabilities to detect threats early.
✅ Strengthening Security and Proactive Defense – Reevaluate user authentication policies, analyze anomalies in network activity, and monitor suspicious processes continuously.
Cyberattacks are becoming increasingly sophisticated, with threat groups leveraging automated tools to exploit vulnerabilities at scale. The fact that Black Basta is actively exploiting 23 critical vulnerabilities poses a significant threat to enterprises and government organizations.
Particularly, vulnerabilities in Cisco IOS XE, Palo Alto PAN-OS, and Microsoft Exchange could serve as open doors for attackers if left unpatched. Organizations must take immediate action to secure their networks and implement proactive cybersecurity strategies to mitigate these evolving threats.



