XWorm and AsyncRAT: Hidden Malware Spreading via PowerShell and Visual Basic
Recent cybersecurity research has shown that malware distribution methods are becoming increasingly sophisticated. A newly discovered batch script is a clear example of this trend.
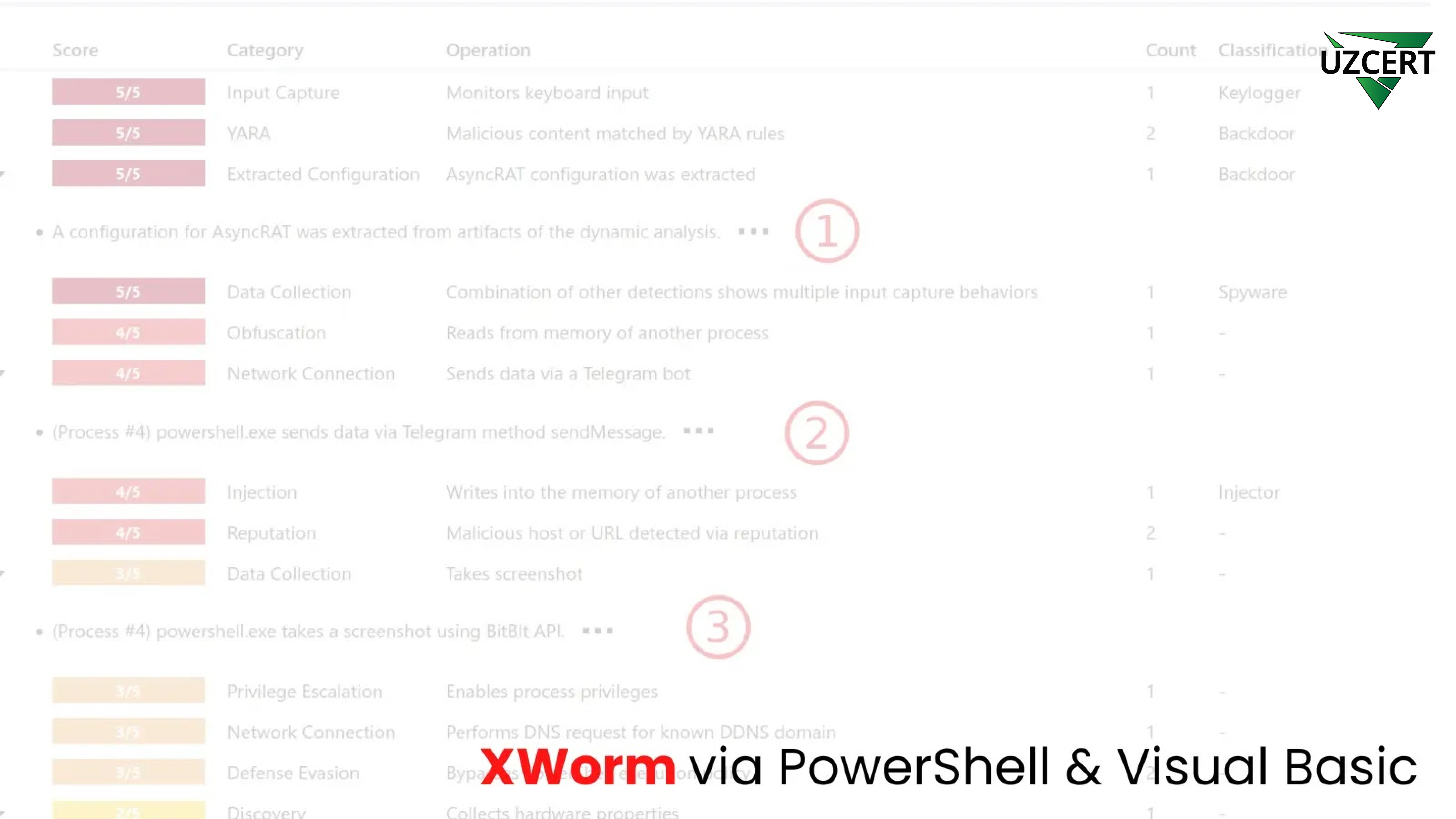
This script is used to distribute powerful malware such as XWorm and AsyncRAT, employing advanced obfuscation techniques to bypass antivirus protections. The fact that this code remained undetected in VirusTotal for two days highlights the severity of the threat.
According to an analysis published by VMRay on X (Twitter), the malicious batch script follows a multi-stage infection chain:
- A PowerShell loader is executed.
- The encrypted malicious payload is decoded and decrypted using AES-256 encryption.
- The decrypted malicious code connects to a Command and Control (C2) server, controlled via Telegram.
- The script collects system information from the victim’s device and sends it to the attacker via Telegram.
The collected information includes:
🔹 Device ID
🔹 Hardware ID (HWID – Hardware Identifier)
🔹 Public IP address and country
🔹 Computer name and username
🔹 Information about installed antivirus software
Additionally, the script can capture screenshots of the victim’s screen and send them to attackers via Telegram.
What Are XWorm and AsyncRAT?
XWorm: A Powerful and Dangerous Trojan
XWorm is a Remote Access Trojan (RAT) that allows attackers to steal user data and remotely control an infected computer. Its key features include:
🔸 Stealing passwords
🔸 Deploying ransomware
🔸 Launching Distributed Denial-of-Service (DDoS) attacks
🔸 Monitoring webcams and recording keystrokes (keylogging)
🔸 Spreading via USB drives
🔸 Bypassing Windows Defender and other security measures
XWorm ensures persistence by modifying the Windows registry and disabling AMSI (Antimalware Scan Interface), making it harder for antivirus programs to detect.
AsyncRAT: A Stealthy Spy
AsyncRAT is another Remote Access Trojan (RAT) with capabilities such as:
🔸 Monitoring and recording the victim’s screen
🔸 Logging keystrokes (keylogging)
🔸 Uploading and downloading files
🔸 Executing commands remotely
🔸 Disabling antivirus software
This malware uses a technique called Process Hollowing, allowing it to inject itself into legitimate Windows processes to evade detection.
This malicious batch script employs advanced obfuscation techniques, including:
🔹 UTF-16 encoding and junk code insertion to make analysis difficult.
🔹 Using open-source obfuscators, making the script nearly unreadable.
🔹 Hiding the PowerShell loader within multiple encryption layers, making it harder for static analysis tools to detect malicious activity.
🔹 Leveraging Telegram as a C2 channel, allowing attackers to remain anonymous.
🔹 Using AI-generated code (e.g., ChatGPT, Claude), making it harder to trace the attack’s origin.
How to Protect Against Such Threats?
💡 Use Behavior-Based Antivirus Solutions – Ensure your security systems can detect unusual activities, such as unauthorized PowerShell execution.
💡 Monitor Network Traffic – Check for connections to unknown IPs and domains, especially those linked to Telegram-based C2 servers.
💡 Train Employees on Phishing Threats – These types of malware are often spread via phishing emails. Educate employees not to click on suspicious links or download unknown attachments.
💡 Regularly Update Your Antivirus Software – Keeping your antivirus software up to date is essential to detect new threats like XWorm and AsyncRAT.
💡 Stay Informed About Emerging Cyber Threats – Follow cybersecurity reports on new malware campaigns and integrate Indicators of Compromise (IoCs) into your security infrastructure.
XWorm and AsyncRAT pose serious cybersecurity risks, continuously evolving with more advanced evasion techniques. Attackers now use batch scripts, PowerShell, and Visual Basic to deploy these malware strains, making traditional antivirus defenses ineffective.
Every IT security professional and system administrator must:
✅ Actively monitor network activity
✅ Implement modern security solutions
✅ Train employees in cybersecurity best practices
⚠️ Stay vigilant and protect your systems from cyberattacks! ⚠️



