
GhostSocks: A New Malware Bypassing Security Systems via SOCKS5 Proxy
The field of cybersecurity faces ever-evolving threats. Recently, a new malware called GhostSocks was discovered, leveraging SOCKS5 proxy technology to bypass security systems and move anonymously across networks. This malicious tool has been thoroughly analyzed by Infrawatch, revealing that it poses a threat to financial institutions and sensitive data.
GhostSocks first appeared in October 2023 on Russian-language hacker forums. It later spread to English-speaking cybercriminals as well. The malware is written in the Golang programming language and operates in conjunction with the LummaC2 infostealer, which not only steals users’ personal data but also turns their systems into proxy servers.
GhostSocks is distributed under the “Malware-as-a-Service” (MaaS) model. Hackers can purchase custom versions of the program for $150 in Bitcoin. Additionally, GhostSocks employs obfuscation technologies such as Garble and Gofuscator to complicate code analysis.
The primary function of GhostSocks is to create a backconnect through the SOCKS5 proxy, allowing cybercriminals to route malicious traffic through infected systems. This method conceals their real IP addresses and facilitates bypassing security measures employed by financial organizations.
Infrawatch researchers identified a malware sample dating back to February 2024, containing the following configuration:
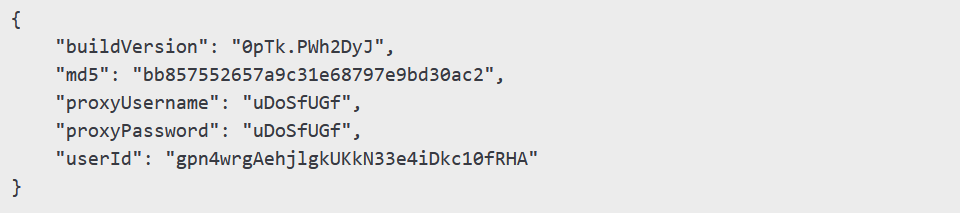
GhostSocks uses a two-tiered command-and-control (C2) server architecture (Tier 1 and Tier 2) to hide traffic. Initial connections occur via HTTP GET requests to the following endpoint:
/api/helper-first-registerEach request contains an X-Api-Key header with an 8-character alphanumeric code (e.g., Fm2qKy29). If authentication fails, the server returns a 403 Forbidden error.
GhostSocks connects to the following IP addresses to continue its malicious activity:
91.142.74[.]28195.200.28[.]33
Additionally, the program includes backdoor modules that allow attackers to:
- Execute commands on the system (
cmd.exe /C); - Steal confidential data;
- Download and execute additional malicious files.
Detection Methods and Precautionary Measures
Infrawatch researchers have developed YARA rules to detect GhostSocks traffic. Here is an example of such a rule:
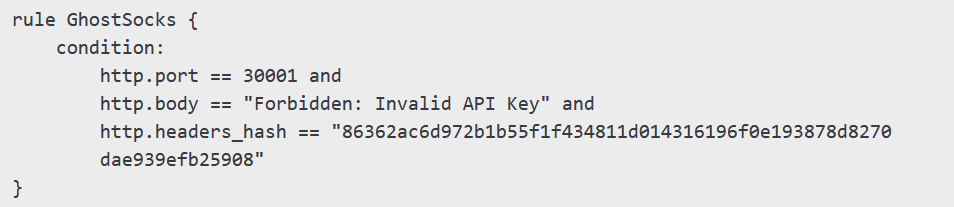
Organizations can protect themselves from the GhostSocks threat by implementing the following measures:
- Network Monitoring: Use YARA rules to detect malicious traffic.
- IP Blocking: Disable IP addresses associated with GhostSocks and servers from AS216071 (VDSina).
- Employee Awareness: Inform cybersecurity professionals about the new threat.
- Antivirus Updates: Utilize modern antivirus solutions and Endpoint Detection and Response (EDR) systems.
- Suspicious Activity Analysis: Monitor abnormal proxy connections and suspicious HTTP requests.
GhostSocks is a dangerous malware actively used by cybercriminals. It exploits SOCKS5 technology to bypass detection systems, not only stealing data but also providing attackers with the ability to move stealthily across networks. Organizations and users must take all necessary precautions to protect their networks and systems from this threat.



