Smart Contract Security: OWASP 2025 Top 10 Vulnerabilities
A smart contract is a digital contract operating on blockchain technology, designed to automatically manage processes when specific conditions are met.
Simply put, a smart contract is a program or a piece of code that ensures the fulfillment of predefined conditions. When these conditions are satisfied, the contract automatically executes the corresponding actions.
Today, smart contracts have become an integral part of financial technologies and the blockchain ecosystem. However, their security remains a pressing issue. OWASP (Open Web Application Security Project) has released a list of the top 10 most critical vulnerabilities in smart contracts for 2025. This document is useful for Web3 developers and security teams, helping them build the necessary skills to prevent vulnerabilities.
With the rapid growth of blockchain technologies and the DeFi (Decentralized Finance) sector, ensuring security has become critically important. OWASP’s list reflects the most relevant attacks and vulnerabilities observed in recent years.
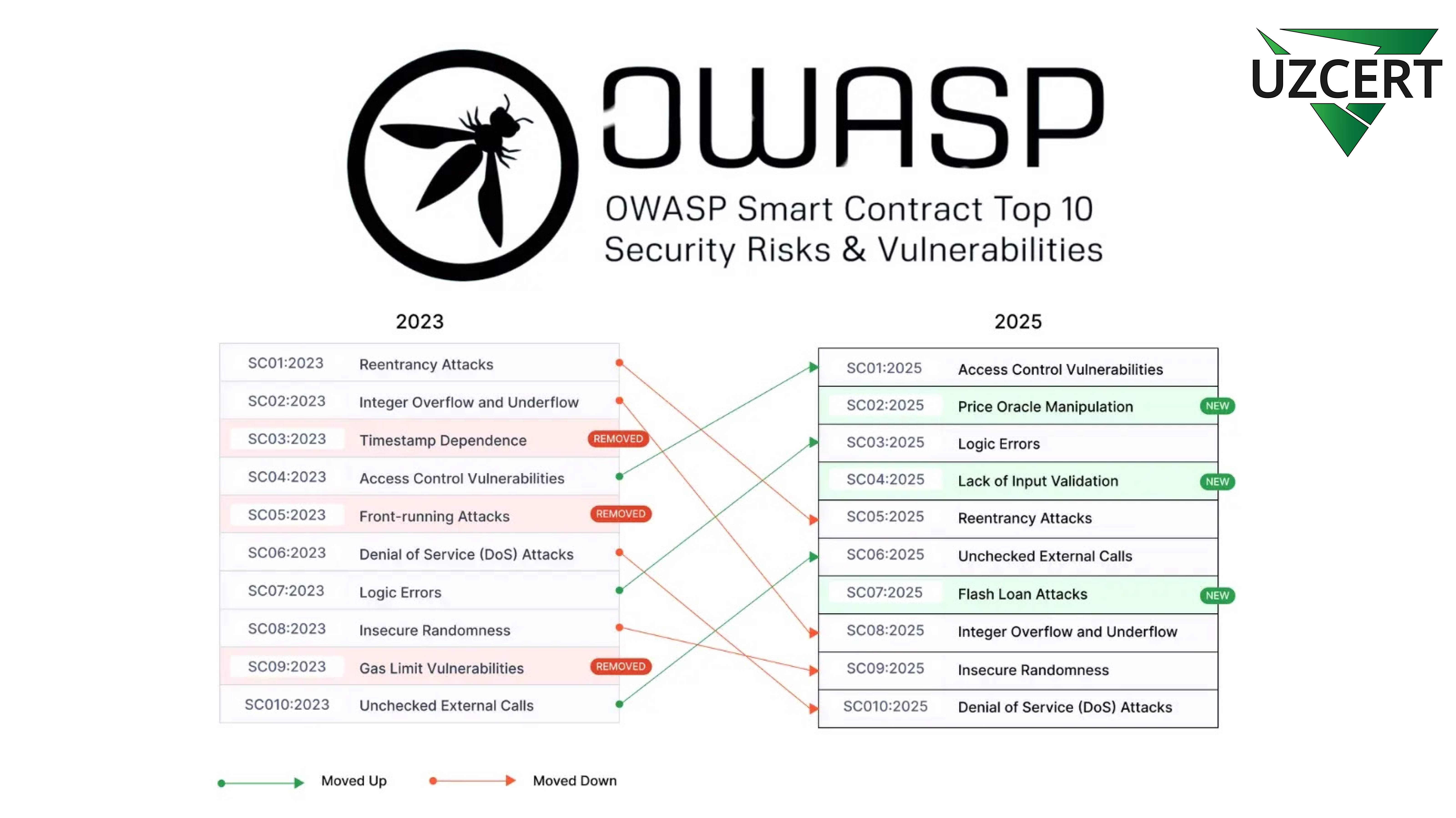
Changes from 2023 to 2025
The 2025 list introduces new vulnerabilities. For example, price oracle manipulation and flash loan attacks have been categorized separately. Vulnerabilities related to time delays and computational resources required for transactions have been combined into new categories.
OWASP Top 10 Vulnerabilities for 2025
- Access Control Vulnerabilities
Access control vulnerabilities often lead to unauthorized access by users or smart contracts. These issues arise from improper rights management or errors in the authentication process.
Mitigations:
- Enforce strict access controls.
- Implement the principle of least privilege.
- Conduct regular code audits.
- Price Oracle Manipulation
Price oracles provide smart contracts with external pricing data. Manipulation of this data can lead to significant financial losses.
Mitigations:
- Use decentralized oracles.
- Calculate prices based on average values.
- Logic Errors
These errors occur when the business logic of a smart contract is flawed, leading to issues like incorrect token issuance or reward distribution.
Mitigations:
- Perform thorough code testing.
- Conduct regular unit tests.
- Lack of Input Validation
Failing to validate inputs allows malicious data to disrupt the functionality of a smart contract.
Mitigations:
- Validate every input.
- Use static and dynamic analysis tools.
- Reentrancy Attacks
These attacks exploit a contract’s external function calls to disrupt ongoing transactions.
Mitigations:
- Avoid calling external functions before updating state variables.
- Use security tools like ReentrancyGuard.
- Unchecked External Calls
Failing to verify whether external calls succeed or fail can lead to incorrect transaction data.
Mitigations:
- Confirm the result of every call.
- Use try/catch blocks.
- Flash Loan Attacks
Flash loans enable borrowing without collateral within a single transaction. Attackers exploit this to harm markets or drain liquidity pools.
Mitigations:
- Limit arbitrage opportunities.
- Monitor operations related to flash loans.
- Integer Overflow and Underflow
Mathematical operations exceeding program limits can cause errors or vulnerabilities.
Mitigations:
- Use libraries like SafeMath.
- Validate inputs and set constraints.
- Insecure Randomness
Improper or predictable generation of random numbers allows attackers to exploit them.
Mitigations:
- Utilize VRF (Verifiable Random Functions).
- Leverage off-chain randomness generators.
- Denial of Service (DoS) Attacks
Attackers overload system resources, disrupting its functionality.
Mitigations:
- Implement resource-limiting policies.
- Avoid or strictly control loops.
In 2024, access control vulnerabilities alone resulted in $953 million in losses. Logic errors caused $63 million in damages, while reentrancy attacks accounted for $35 million. These figures underscore the urgent need to enhance smart contract security.
The OWASP Top 10 for 2025 serves as a valuable resource for developers and security specialists. By studying this document, one can prioritize security at every stage of code development.
The future of blockchain technologies depends on security. Therefore, adopting best practices in Web3 projects helps build trust among users and investors.



