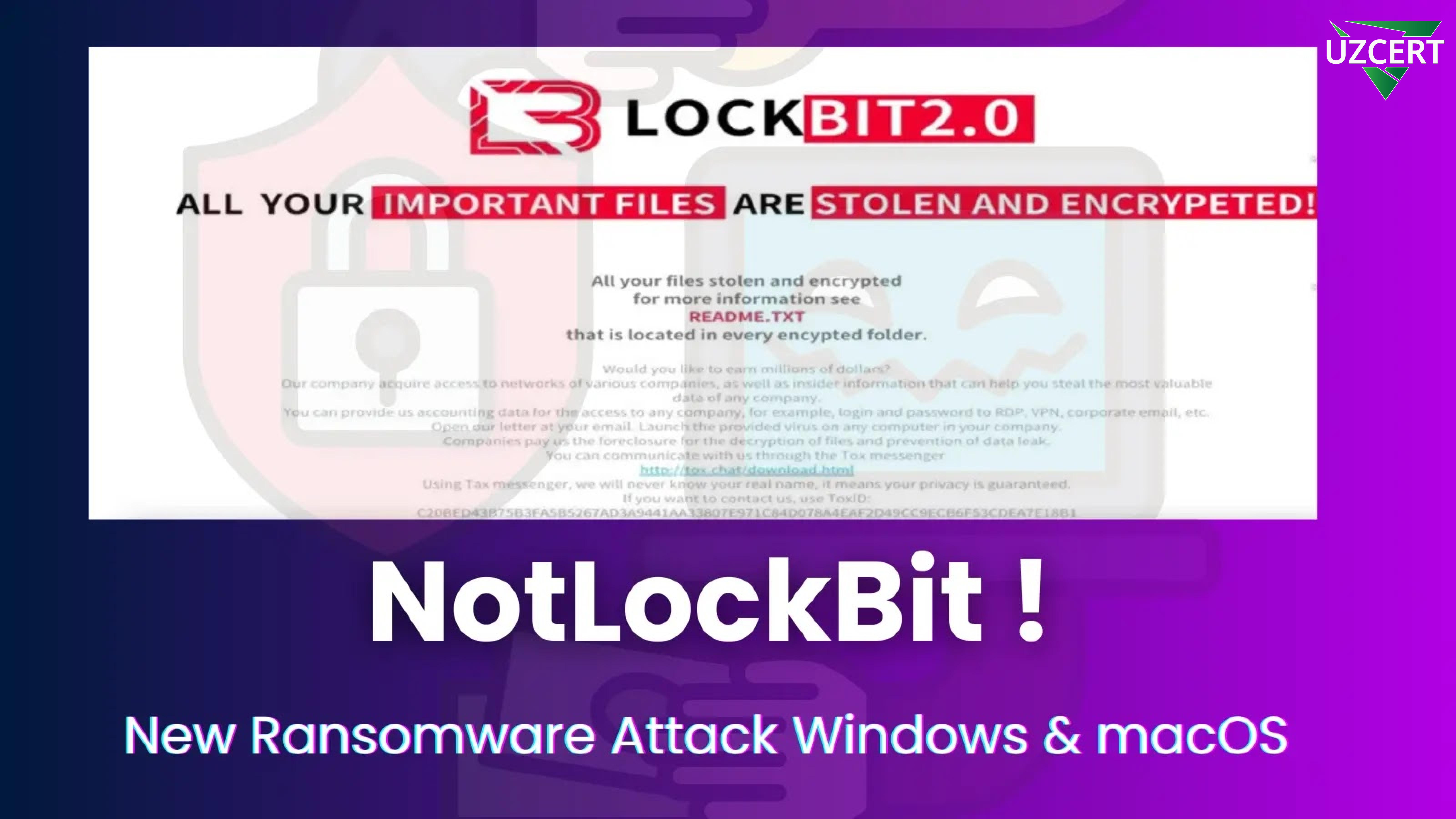
“NotLockBit” — A New Ransomware Targeting Windows and macOS Systems
A new, highly sophisticated ransomware family named “NotLockBit” is making waves in the cybersecurity field. Mimicking the style of the infamous LockBit ransomware, this malicious software poses a significant threat with its advanced capabilities and cross-platform functionality, targeting both Windows and macOS systems. NotLockBit adapts its attacks using tailored strategies for each operating system.
Distributed as an x86_64 binary file written in the Go programming language, NotLockBit offers the following advanced features:
- Data Encryption: It employs strong encryption protocols like AES and RSA to encrypt critical data, which can only be recovered with a special key controlled by the attackers.
- Data Theft: User data is uploaded to storage services controlled by attackers, such as Amazon S3. This enables a double extortion strategy, threatening both data loss and exposure.
- Self-Destruction Mechanism: The ransomware removes its traces, including shadow copies and executable files, making system recovery nearly impossible.
Once executed, NotLockBit initiates a reconnaissance phase, particularly optimized for macOS environments. Using the Go-sysinfo module, the malware gathers the following information:
- Hardware specifications;
- Operating system version;
- Network configurations;
- Unique device identifiers (UUID).
The encryption process occurs in multiple stages:
- The embedded RSA public key is decoded from a PEM file.
- A random master encryption key is generated and encrypted using the RSA key.
- User files are encrypted and saved under new names with a
.abcdextension, while the original files are deleted.
During the encryption process, critical system directories (e.g., /proc/, /sys/, /dev/) are excluded, indicating the ransomware’s focus on user data rather than system files.
NotLockBit targets the following file types:
- Personal Documents: .doc, .pdf, .txt;
- Work Files: .csv, .xls, .ppt;
- Multimedia: .jpg, .png, .mpg;
- Virtual Machine Data: .vmdk, .vmsd, .vbox.
This selection highlights the ransomware’s intent to focus on high-value data.
On macOS systems, NotLockBit uses the osascript command to change the desktop wallpaper, visually displaying the ransom note to the user.
In the final stage, the ransomware self-destructs by:
- Deleting its executable file from the system;
- Erasing shadow copies to disable recovery options.
Due to its high level of sophistication, combating NotLockBit requires robust security measures for detection and mitigation. The cybersecurity company Qualys has confirmed that its EDR and EPP solutions can detect and quarantine the ransomware during the download phase.
To protect against threats like NotLockBit, the following measures are recommended:
- Regular Backups: Keep critical data backed up offline to ensure recovery options remain available.
- Endpoint Protection: Deploy advanced detection systems to identify malicious activities early.
- Network Security: Implement firewalls, IDS systems, and strict access controls.
- Employee Training: Conduct training sessions to help staff recognize phishing and social engineering attacks.
NotLockBit’s cross-platform functionality, data theft capabilities, and self-destruction mechanism underscore the sophistication of modern ransomware attacks. Cybersecurity professionals must remain vigilant and prepared for such threats. Comprehensive protection, active monitoring, and continuous education play vital roles in mitigating these complex risks.



