CoinLurker: Next-Generation Tool Used in Modern Cyberattacks
CoinLurker is an advanced data-stealing malware that has revolutionized fake update campaigns. Written in the Go programming language, CoinLurker utilizes obfuscation and anti-analysis techniques, enabling it to evade detection and carry out stealthy cyberattacks.
According to Morphisec’s report, CoinLurker has become a key weapon for cybercriminals targeting cryptocurrency wallets, sensitive user data, and financial applications.
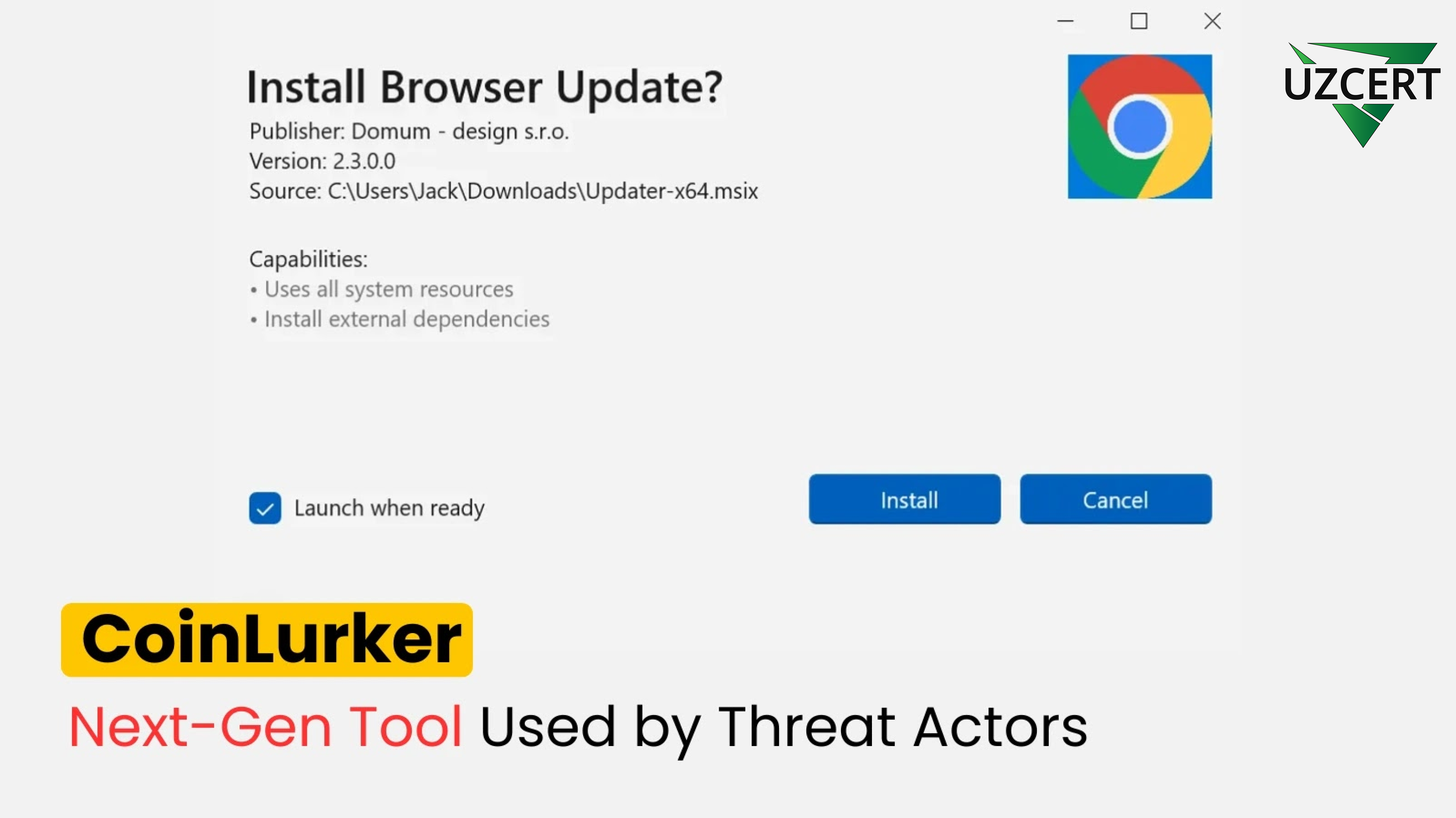
Like previous threats, CoinLurker employs fake updates and deceptive notifications to infect devices. The main infection methods include:
- Fake software updates:
Malicious websites prompt users to download “updates” disguised as legitimate patches. - Malvertising (malicious advertising):
Compromised ads redirect users to websites hosting fake updates. - Phishing emails:
Links in phishing emails lead victims to fake update pages. - Social media links:
Malicious links shared on social media platforms direct users to fake verification or update pages.
CoinLurker uses advanced techniques to avoid detection and maximize damage. Key methods include:
- EtherHiding Technology:
CoinLurker conceals malicious payloads within blockchain infrastructure, bypassing traditional security mechanisms. - Multi-Stage Delivery Process:
- Binance Smart Contracts: Attackers embed malicious instructions in Binance Smart Contracts, leveraging the decentralized and tamper-proof nature of blockchain.
- C2 (Command-and-Control) Servers: Malware dynamically fetches commands from attacker-controlled servers, avoiding static indicators that could trigger detection.
- Bitbucket Repositories: Initially, safe files are hosted on Bitbucket repositories, later replaced with malicious versions, exploiting Bitbucket’s reputation as a trusted platform.
- Microsoft Edge WebView2:
This component acts as a stager, mimicking legitimate browser update tools to distract users while delivering the payload. - Memory Execution and String Encryption:
CoinLurker executes its malicious code in memory, leaving minimal traces on disk and making detection much more difficult.
CoinLurker specifically targets cryptocurrency wallets and financial applications.
- It gathers system information using commands like systeminfo, ipconfig /all, and route print.
- Stolen data is transferred to C2 servers.
- The malware hides infected files in concealed folders, downloading additional malicious payloads as needed.
To effectively defend against CoinLurker, follow these cybersecurity best practices:
- Keep antivirus and security software updated:
Use advanced antivirus solutions and regularly apply software patches. - Train employees on cybersecurity awareness:
Educate staff to recognize phishing emails and fake software update prompts. - Monitor for suspicious network traffic:
Use tools to analyze network activity and implement DNS filtering to block known malicious domains. - Use Data Loss Prevention (DLP) tools:
DLP systems help detect and prevent unauthorized data transfers.
CoinLurker highlights the increasing sophistication of modern cyberattacks, particularly against cryptocurrency users. Its ability to conceal payloads via blockchain technology and dynamically deliver malware makes it a significant threat.
Both individuals and organizations must adopt proactive security measures to defend against threats like CoinLurker. Strengthening cybersecurity awareness, applying regular updates, and deploying robust defense tools are critical to staying protected.



