
CL0P Ransomware Group Conducts Large-Scale Attacks on Telecommunications and Healthcare Sectors
The CL0P ransomware group has intensified its attacks against critical infrastructure sectors, leading to widespread data breaches and system encryptions in telecommunications and healthcare organizations worldwide.
By exploiting a newly discovered zero-day vulnerability (CVE-2024-50623) in Cleo integration software, the attackers successfully breached over 80 organizations within a single month (February 2025). This marks a significant increase compared to their 384 attacks in 2023.
The CL0P group exploits vulnerabilities in file-sharing systems, stealing sensitive patient data, billing system information, and network configurations before encryption. Their latest tactic combines automated exploitation scripts with manual lateral movement, specifically targeting unpatched, internet-exposed systems.
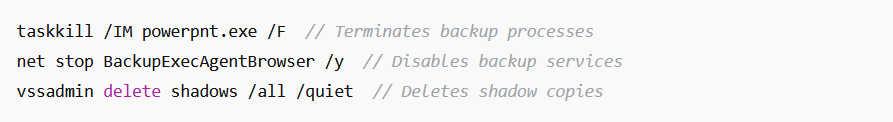
According to Cyberint security experts, the attackers use the following commands to prevent system recovery:
CVE-2024-50623 Exploitation
In February 2025, CL0P’s attacks primarily leveraged CVE-2024-50623, a vulnerability found in Cleo’s LexiCom, VLTrader, and Harmony platforms—commonly used for healthcare data exchange and telecommunications billing systems.
Using Cleo’s HTTP API, attackers deploy malicious DLL files to gain full system control.
CL0P’s Attack Chain
- Initial access via Cleo vulnerabilities.
- Credential harvesting.
- Data exfiltration over 72–96 hours.
- Deployment of encryption binaries (separate RSA keys for each victim).
Encrypted files now bear the .Cl0p_2025 extension, with Clop^_- hexadecimal markers, making them easier to identify.
The CL0P group has transitioned to anonymous ransom payments via a Tor-based chat portal. This shift coincided with their February 12, 2025, update to distribute stolen data via torrent networks.
Over 22 TB of stolen data from healthcare insurers and telecom providers has been leaked across peer-to-peer (P2P) networks, including:
- 3.1 million patient records with Social Security numbers and medical histories.
- 5G network topology maps of Asian telecommunications operators.
- Medical device firmware from U.S. hospitals.
Alongside CVE-2024-50623, CL0P is exploiting:
- CVE-2021-27101 (SQL Injection).
- CVE-2021-27104 (Remote Command Execution).
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) recommends updating Cleo software to version 5.8.0.21, but experts advise implementing additional security measures.
Security teams should monitor for:
vssadmin resize shadowstoragecommand execution.- TLS traffic to
hiperfdhaus.com(CL0P’s known C2 domain).
Recommended Security Measures
🔹 Keep Systems Updated
- Upgrade Cleo software to the latest version.
- Apply all security patches promptly.
🔹 Protect Backup Systems
- Implement additional backup protection measures.
- Store backups in offline environments.
🔹 Network Segmentation
- Isolate critical systems to limit lateral movement.
🔹 Employee Training
- Conduct training sessions on phishing attacks and cyber threats.
🔹 Security Audits
- Perform regular security assessments to identify and remediate vulnerabilities.
The CL0P ransomware group has escalated its attacks on telecommunications and healthcare sectors, causing severe disruptions. Due to the interconnected nature of critical infrastructure, these attacks pose a growing risk.
To mitigate threats, organizations must prioritize system updates, backup protection, and staff awareness.
Cybersecurity is a continuous process that requires vigilance and proactive defenses. To combat groups like CL0P, organizations must adopt a strategic approach and prioritize security at every level.



