
Ghost Ransomware: CISA and FBI Warn of Threats to Organizations in Over 70 Countries
The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) have jointly issued a warning about large-scale attacks carried out by the Ghost ransomware group. This group has targeted organizations across more than 70 countries, spanning various sectors. Operating under aliases such as Cring, Crypt3r, and Phantom, the group is believed to have ties to China. They exploit vulnerabilities in outdated software to spread ransomware variants like Ghost.exe and Cring.exe.
The attacks are aimed at critical sectors, including healthcare, government agencies, education, and manufacturing. The group employs sophisticated techniques such as disabling security protocols, encrypting data, and demanding ransom payments in cryptocurrency.
Ghost leverages vulnerabilities listed in the Common Vulnerabilities and Exposures (CVEs) database to gain access to networks. Their primary targets are unpatched systems. Key vulnerabilities exploited include:
- CVE-2018-13379: A vulnerability in Fortinet FortiOS devices.
- CVE-2010-2861 & CVE-2009-3960: Vulnerabilities in Adobe ColdFusion servers.
- CVE-2021-34473, CVE-2021-34523, CVE-2021-31207: Microsoft Exchange server vulnerabilities (used in ProxyShell attack chains).
By exploiting these vulnerabilities, attackers can deploy web shells and execute malicious programs using PowerShell or Command Prompt.
Once inside a network, the Ghost group disables security features using the following PowerShell commands:
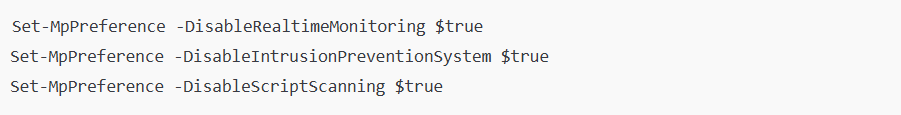
This script disables Windows Defender’s real-time monitoring, intrusion prevention, and script scanning. The attackers then deploy ransomware such as ElysiumO.exe or Locker.exe to encrypt files. During encryption, critical system directories are bypassed to prevent complete system failure. Additionally, Volume Shadow Copies and Windows Event Logs are deleted to make data recovery more difficult.
The Ghost group utilizes penetration testing tools like Cobalt Strike Beacon to establish communication with command-and-control (C2) servers via HTTP/HTTPS protocols. They use platforms like Mega.nz and Cobalt Strike Team Servers for data exfiltration, although their primary tactic is to threaten data exposure rather than conducting large-scale data theft.
Ghost prioritizes speed, often completing the process from initial access to ransomware deployment within hours. They move laterally within networks using tools like:
- Windows Management Instrumentation Command-Line (WMIC)
- PowerShell scripts
For example, they execute encoded PowerShell commands to load Cobalt Strike Beacon directly into memory, allowing stealthy execution:

They also use tools such as SharpShares and Ladon 911 to scan for network resources and exploit SMB vulnerabilities.
Mitigation Strategies and Recommendations
1. Patch Management:
- Immediately patch vulnerabilities like CVE-2018-13379 and ProxyShell exploits.
2. Network Segmentation:
- Segment the network to limit lateral movement from compromised devices.
3. Multi-Factor Authentication (MFA):
- Enforce MFA on all privileged accounts and email services to prevent phishing-based attacks.
4. Secure Backups:
- Maintain offline and immutable backups to enable ransomware-free recovery.
Additional Security Measures
- Monitor PowerShell Activity: Continuously track unauthorized PowerShell script execution.
- Behavioral Analysis: Use behavioral detection tools to identify ransomware indicators, such as mass file encryption and log deletion.
- Follow CISA Guidelines: Implement Cross-Sector Cybersecurity Performance Goals (CPGs) and adopt a layered defense strategy.
The Ghost ransomware group poses a severe global threat. Organizations can protect themselves from this and similar cyberattacks by following the recommended security practices, ensuring timely patching, enforcing network segmentation, and implementing strict access controls. Additionally, staying informed through initiatives like #StopRansomware is crucial for maintaining cybersecurity.
Further Protective Measures
- Employee Awareness Training: Educate staff about phishing and other cyber threats.
- Regular Security Updates: Keep antivirus, network security, and other defense tools up to date.
- Third-Party Security Audits: Engage cybersecurity experts to assess security posture and identify vulnerabilities.
By implementing these measures, organizations can significantly enhance their resilience against cyber threats.



