
Advanced System Against APT Threats: Have You Heard About EARLYCROW?
Today, one of the most significant threats in the field of cybersecurity is Advanced Persistent Threats (APTs). These attacks target government agencies, major corporations, research centers, and military organizations, carrying out covert and long-term operations.
APT threats utilize sophisticated malware such as:
🔹 Remote Access Trojan (RAT) – Malicious software that allows remote control over an infected system.
🔹 Rootkits – Hidden programs that deeply integrate into a system to evade detection.
🔹 Spyware – Malware designed to collect confidential information.
🔹 Keyloggers – Programs that record a user’s keystrokes to steal credentials.
These tools enable cybercriminals to steal sensitive data, infiltrate networks, and maintain control over compromised systems.
Such malware communicates with Command-and-Control (C&C) servers over HTTPS traffic, making it difficult to detect using traditional Network Intrusion Detection Systems (NIDS) due to the encryption used in these communications.
Researchers Almuthanna Alageel and Sergio Maffeis from Imperial College London have developed EARLYCROW, a system specifically designed to detect APT threats operating over HTTPS.
EARLYCROW uses contextual analysis of network traffic to identify suspicious activities without decrypting HTTPS traffic.
This system introduces a multi-purpose network flow format called PairFlow, which analyzes traffic behavior and statistical patterns to detect hidden C&C activities.
How Does EARLYCROW Work?
🔹 Contextual Summaries
EARLYCROW analyzes HTTPS traffic without decrypting it, summarizing key attributes using the PairFlow format to detect anomalies.
🔹 Threat Model
The system is built based on tactics, techniques, and procedures (TTPs) used by APT groups, making it highly effective in detecting their activities.
🔹 High Accuracy
EARLYCROW achieves an impressive 93.02% detection accuracy with a false positive rate (FPR) of just 0.74%.
APT Detection Process Using EARLYCROW
1️⃣ Capturing network traffic in PCAP format
2️⃣ Converting data into the PairFlow format
3️⃣ Analyzing PairFlow features using machine learning models
4️⃣ Detecting suspicious C&C activity and alerting security teams
Example Code for Converting PCAP to PairFlow (Python)
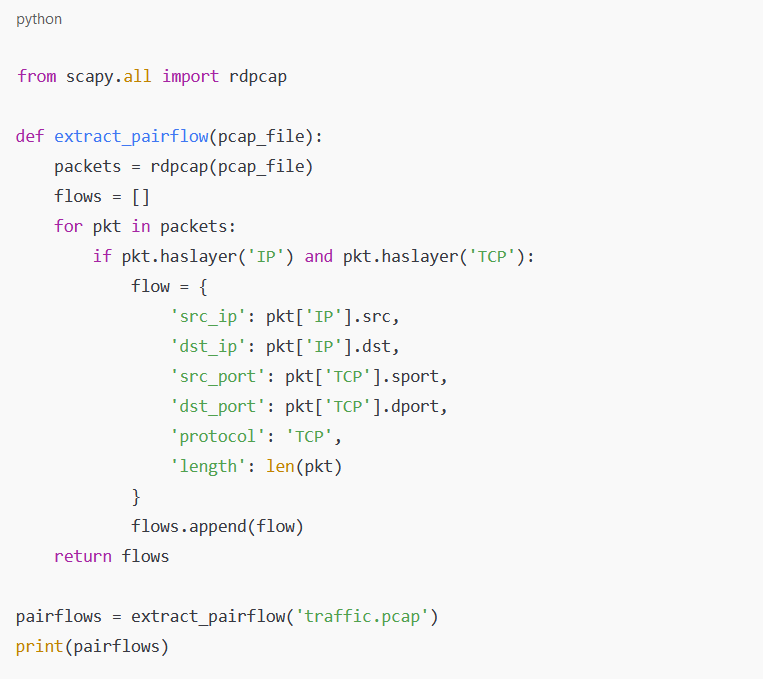
This Python script extracts key network traffic attributes, enabling analysis using the PairFlow format.
Impact of EARLYCROW on Cybersecurity
✅ Early detection of APT threats – Identifies encrypted C&C communications that traditional NIDS might overlook.
✅ Adaptability to new threats – Machine learning models allow the detection of previously unknown APT attacks.
✅ Analyzing HTTPS traffic without breaking encryption – Ensures privacy while accurately identifying malicious activities.
Future Development of EARLYCROW
🔹 Support for other encrypted protocols – Researchers plan to extend EARLYCROW’s capabilities to TLS 1.3, QUIC, and VPN traffic.
🔹 Integration with existing NIDS solutions – Compatibility with Snort, Suricata, and Zeek for enhanced security.
🔹 Cloud infrastructure adaptation – Automated network traffic analysis for AWS, Azure, and Google Cloud Platform.
Conclusion
EARLYCROW is an innovative approach to detecting APT threats over HTTPS, offering:
✅ Detection of hidden C&C communications that traditional security systems often miss.
✅ Early-stage identification of APT attacks, helping organizations proactively protect themselves.
✅ Accurate monitoring of encrypted traffic without compromising data privacy.
In today’s rapidly evolving cyber threat landscape, where industry leaders like Check Point and Wiz are developing cutting-edge security solutions, EARLYCROW is set to become a vital component of modern cybersecurity infrastructure.
This technology marks a new era in cybersecurity and serves as a powerful weapon against APT groups.



